
 en
en  Español
Español  中國人
中國人  Tiếng Việt
Tiếng Việt  Deutsch
Deutsch  Українська
Українська  Português
Português  Français
Français  भारतीय
भारतीय  Türkçe
Türkçe  한국인
한국인  Italiano
Italiano  Indonesia
Indonesia  Polski
Polski There are tasks where standard HTTP(S) proxies fall short: low-latency online gaming; VoIP calls and streaming that demand stable connections; high-throughput P2P and torrenting; and automation or web scraping that must handle multiple connection types. In these cases, SOCKS5 proxy provides a flexible, capable option that supports various internet protocols, making it ideal for web browsing and maintaining online privacy.
This article covers what SOCKS5 is used for, how it works, where it’s used, and its main strengths and limitations.
It is a server that speaks version 5 of the SOCKS protocol. It relays network traffic through a remote endpoint and substitutes the originating IP address, enabling strong online anonymity, stable internet connection, and flexibility across a wide range of applications and services.
Because it relies on the SOCKS5 protocol, it supports the following capabilities:
SOCKS5 proxy servers support IPv6, expanding the available address pool and easing work with modern networks. They are available as datacenter, residential, ISP, and mobile options, making them adaptable to different workloads.
The high-level flow below shows how authentication, authorization, packet forwarding, and IP substitution are implemented:
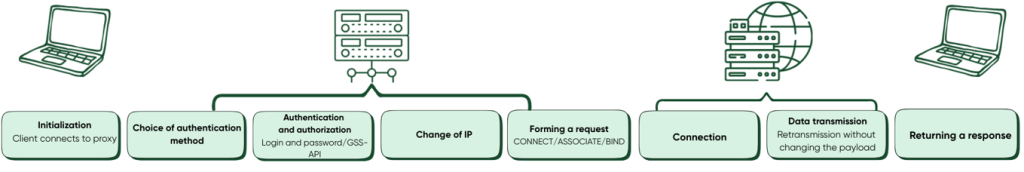
This routing supports both TCP and UDP, including non-standard protocols and packet types, while preserving packet structure. That’s a key difference from HTTPS proxies, which handle TCP only and may alter HTTP headers.
To use it, specify the intermediary’s IP address, port, and authentication data (if used) in your OS network settings or directly in the application if it supports it natively.
Real-world scenarios illustrate when this protocol helps and can inform a decision in its favor:
These aren’t a universal answer, but in scenarios where HTTP(S) ones are limited, they often perform better. Transport-level operation with TCP and UDP and transparent routing make them a strong fit for workloads with strict latency, stability, and packet-integrity requirements. Effectiveness depends on its type: datacenter options favor speed; residential and ISP options are more resilient to filtering; mobile options offer the greatest variability.
To get the expected results with SOCKS5, consider two points: add separate encryption for sensitive data when needed, and route traffic correctly for applications that don’t use system proxy settings. SOCKS5 makes sense when you need both flexibility and performance; success depends on how well it’s integrated into your infrastructure and tailored to the specific task.
HTTP(S) handle only web traffic and may modify HTTP headers. SOCKS5 transparently forwards packets of any protocol (TCP/UDP) without changing headers.
No. By default, it does not encrypt data. For confidential traffic, it’s often paired with SSH tunnels or other encryption tools.
Yes. It works with both IPv4 and IPv6, which expands the address pool and helps mitigate IPv4-related limitations.
Username/password, IP-based allowlisting, or Kerberos (GSS-API). The method depends on the proxy server’s security policy.
The protocol itself doesn’t impose a speed cap; its role is transport-level routing. Performance depends on intermediary type and provider infrastructure. Datacenter IPs minimize latency; residential and mobile may be slower but offer greater realism and stability for traffic patterns.
Comments: 0