
 en
en  Español
Español  中國人
中國人  Tiếng Việt
Tiếng Việt  Deutsch
Deutsch  Українська
Українська  Português
Português  Français
Français  भारतीय
भारतीय  Türkçe
Türkçe  한국인
한국인  Italiano
Italiano  Indonesia
Indonesia  Polski
Polski KDE, short for K Desktop Environment, is a Linux desktop environment that provides a graphical user interface shell. Configuring a private proxy in KDE can be done either through the system interface or via the terminal. This enables you to route your Internet traffic, bypass regional restrictions, change your IP address to access blocked platforms, and surf the web anonymously.
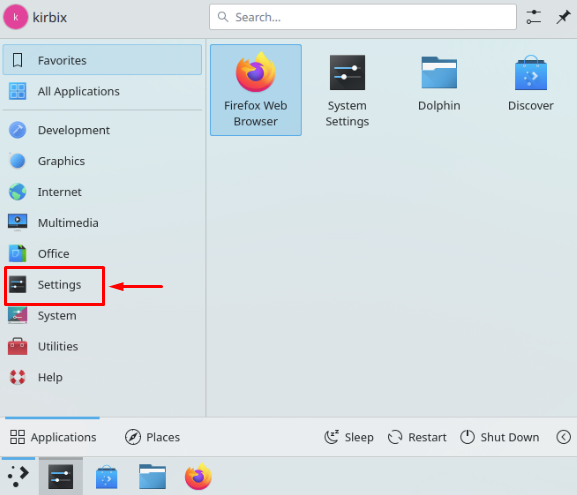
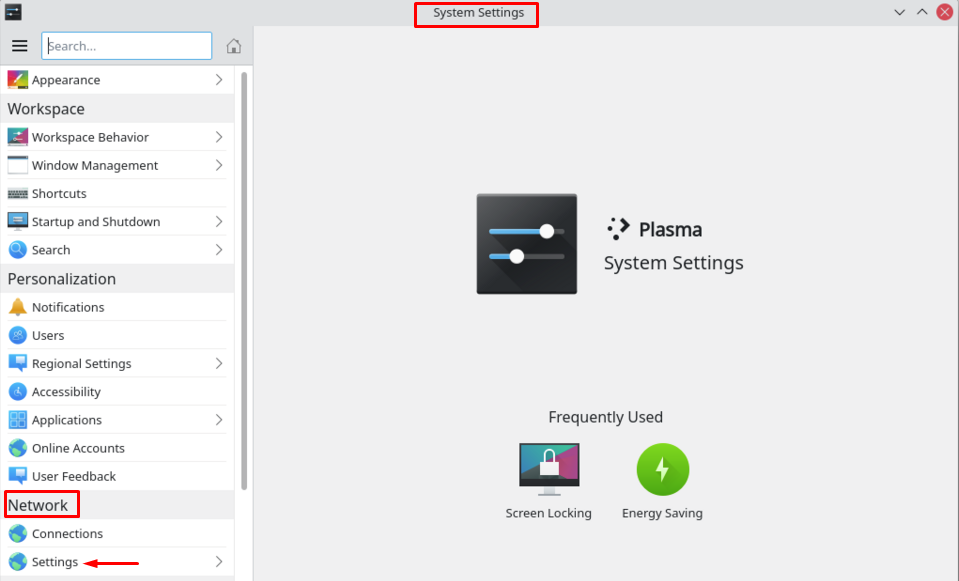
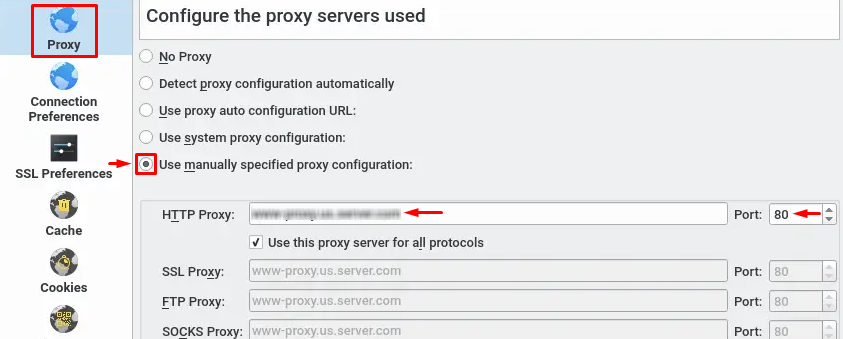
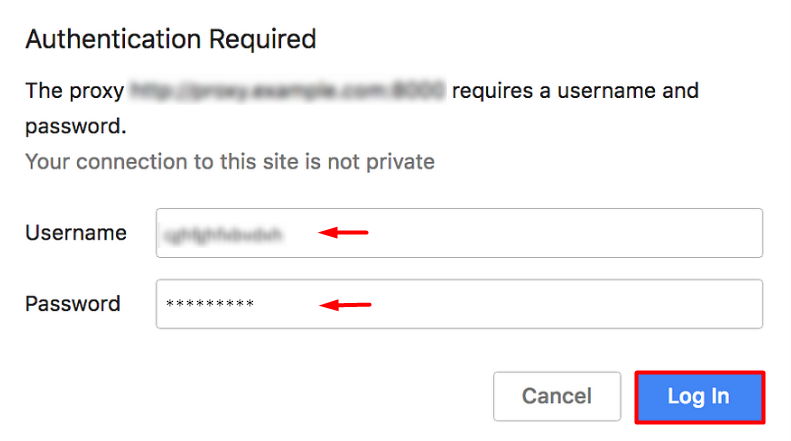
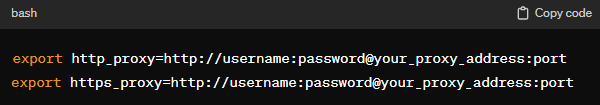
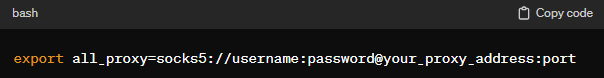
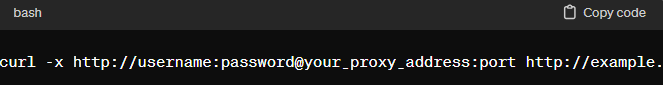
When configuring proxies in the KDE environment, it’s important to understand that KDE itself does not impose strict limitations. It relies on Linux system-wide network settings, which means standard HTTP, HTTPS, and SOCKS proxies are fully supported.
Static types are best configured at the system level. Dynamic ones are less suitable for full system-wide configuration. Frequent IP rotation can disrupt active connections and system services. For these cases, it’s better to use proxy managers or per-application settings, allowing traffic to be routed selectively and IP changes to be handled without breaking the entire system.
The setup is complete, and you can now use KDE proxies to access previously inaccessible resources and bypass other restrictions.
Comments: 1