
 en
en  Español
Español  中國人
中國人  Tiếng Việt
Tiếng Việt  Deutsch
Deutsch  Українська
Українська  Português
Português  Français
Français  भारतीय
भारतीय  Türkçe
Türkçe  한국인
한국인  Italiano
Italiano  Gaeilge
Gaeilge  اردو
اردو  Indonesia
Indonesia  Polski
Polski Tor is a browser designed for secure internet usage, bypassing regional restrictions, and accessing blocked websites. The browser features a unique routing system, allowing users multiple layers of protection for complete anonymization of their online activities. For instance, an internet provider cannot track the websites visited through the Tor browser; it only sees outgoing connections from the Tor network. One additional method to conceal your location and bypass restrictions is by using proxy servers.
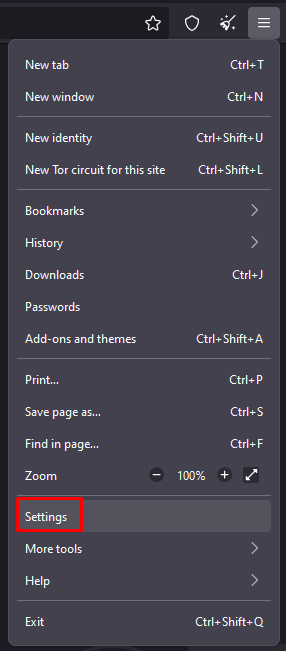
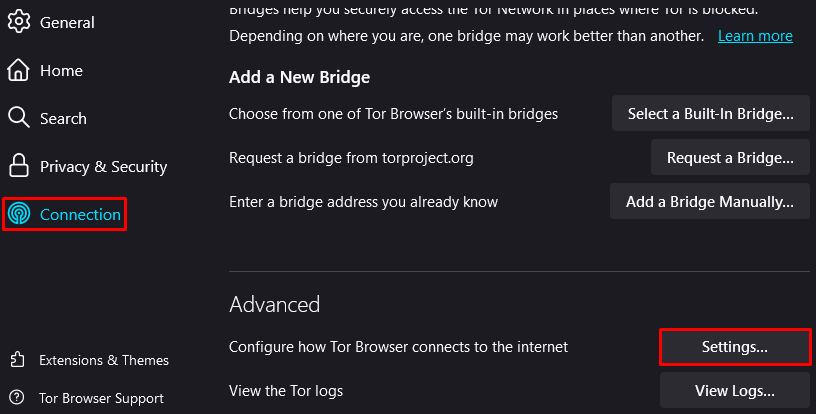
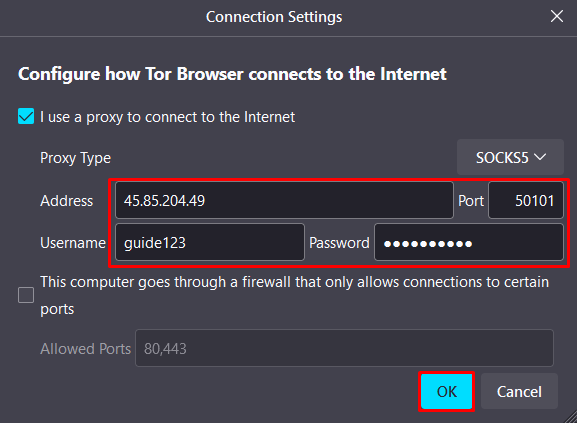
Done, the proxy is configured and ready to use. The TOR browser provides a high level of connection anonymization, but using a proxy server can further enhance this measure.
Comments: 0