
 en
en  Español
Español  中國人
中國人  Tiếng Việt
Tiếng Việt  Deutsch
Deutsch  Українська
Українська  Português
Português  Français
Français  भारतीय
भारतीय  Türkçe
Türkçe  한국인
한국인  Italiano
Italiano  Gaeilge
Gaeilge  اردو
اردو  Indonesia
Indonesia  Polski
Polski The use of Zoom may be restricted in various areas or networks. Some common reasons include administrative controls or geographic limitations. With a Zoom proxy server, you may be able to bypass such barriers, depending on local firewall and ISP policies. It reroutes the platform's traffic through an alternate IP address. This configuration can enable access to geo-restricted meetings and improve privacy by masking your public IP on any device.
In corporate environments, an intermediary server improves control over connection endpoints. It reduces the exposure to unwanted traffic. Using an intermediary can help maintain stability in restricted networks, but security still relies on the platform's end-to-end TLS. For example, when accessing sensitive tools such as video conferencing platforms, Zoom users should have proper Zoom account credentials, and configuring the connection through an intermediary server ensures both security and accessibility. The steps below show how to configure one via Proxifier.
The following are the effective steps to set up a Zoom proxy. This step-by-step guide will help you with a stable connection and ensure your Zoom application runs smoothly and securely:
Firstly, get Proxifier and click the Profile tab in the main menu. Next, select Proxy Servers.
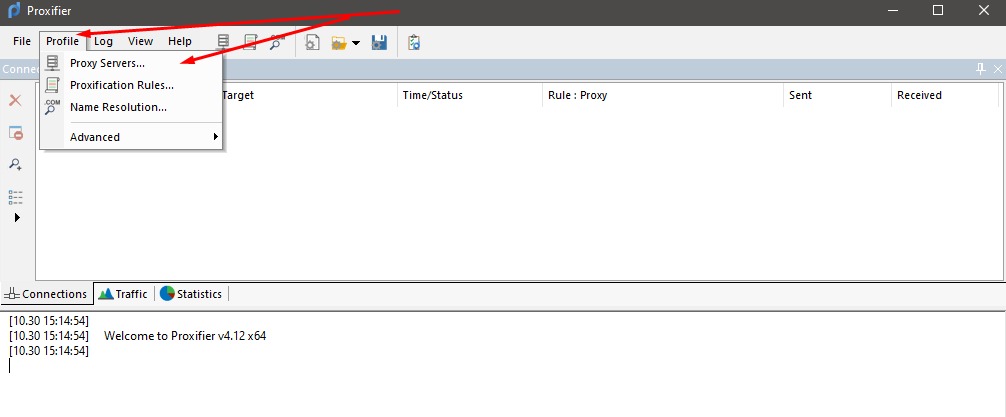
Now, click Add.
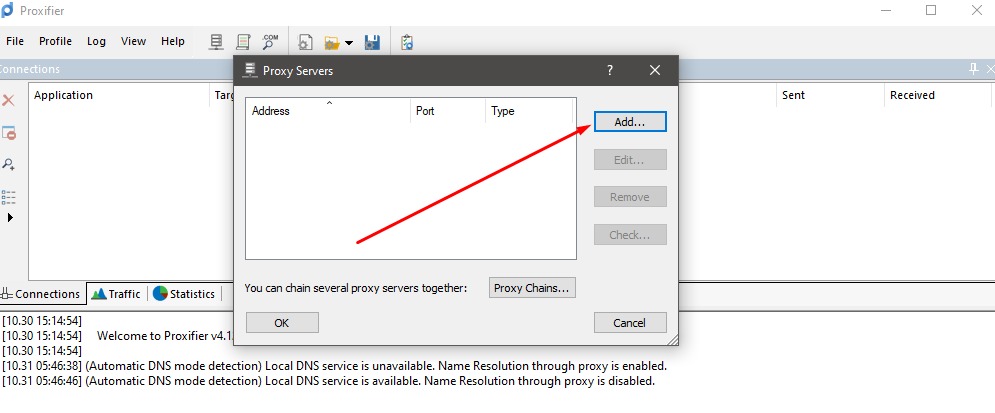
The connection's IP address and the port need to be entered. Next, choose the connection protocol. SOCKS5 is generally recommended because it supports UDP/VoIP traffic; some HTTP/HTTPS protocols may not support all platform's features. If your new IP requires credentials, enable Authentication and enter the username/password from your provider. And, click OK.
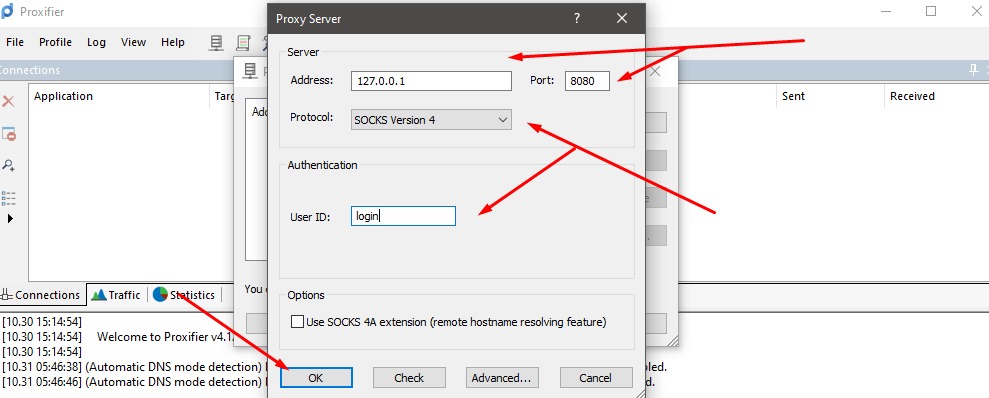
In this step, get back to the Profile tab. And, choose Proxification Rules.
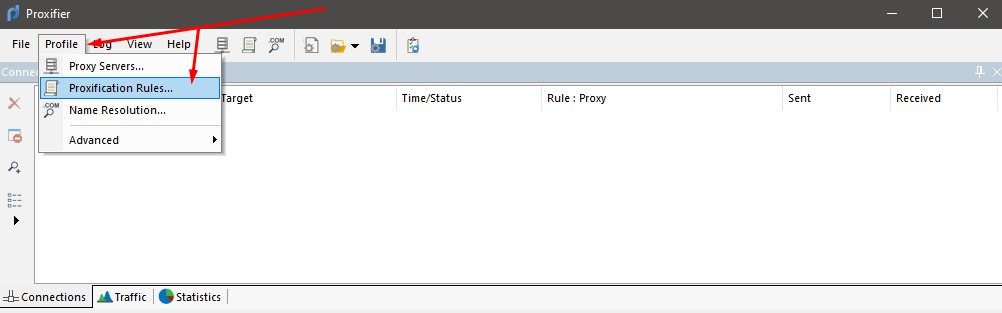
Now, go to the window displaying connections. Click the Add button at the bottom. The next part is to click Browse and locate the executable file. Choose the .exe file or the program shortcut.
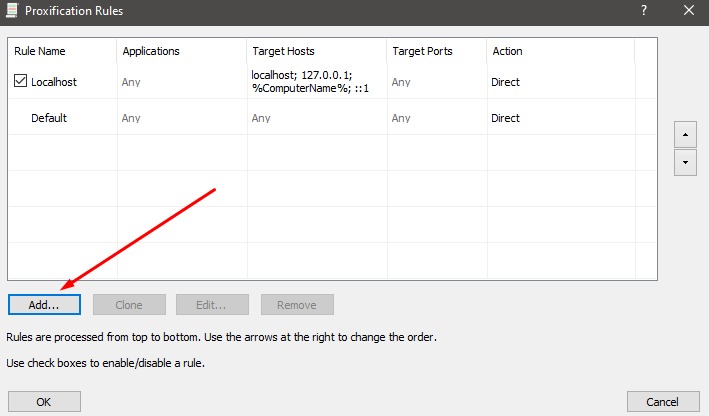
Finally, select the configured server in the Action field and click OK.
The following are some significant advantages of using a Zoom proxy:
There are several issues that may occur when you want to use a Zoom proxy. Gaining proper knowledge of these issues and their resolutions can help ensure a smooth connection:
ISSUE 1: Incorrect settings
The platform may not be able to connect if the intermediary host or port is incorrect.
Resolutions:
ISSUE 2: Authentication error
When the intermediary server needs login credentials, your software may not be connected.
Resolutions:
ISSUE 3: Unsupported protocols
There is a possibility that this platform may not work with all protocol types.
Resolutions:
ISSUE 4: Firewall or antivirus blocking
Another common problem is that a security software might interrupt the intermediary server traffic of your app.
Resolutions:
ISSUE 5: Network or ISP-level restrictions
Some users may also see that their ISP or local network blocks the server connections.
Resolutions:
A Zoom proxy setup is a practical way to improve privacy and maintain access in restricted networks by masking your public IP. It maintains the user's anonymity and offers access to the platform in restricted areas. The users can gain control over the traffic flow after changing Zoom proxy settings in the platform. Besides, there will be a reduced exposure to external threats. This is valuable for teams that are working under network limitations.
Moreover, a trusted service supports stable performance when it is integrated with a reliable environment. So, instead of relying on general privacy tools, a Zoom proxy configuration created a targeted layer of control. It aligns with location, security, and compliance needs across diverse use cases. It aligns with location, security, and compliance needs across diverse use cases, making it easier for users to join meetings and collaborate securely.
Comments: 0