
 en
en  Español
Español  中國人
中國人  Tiếng Việt
Tiếng Việt  Deutsch
Deutsch  Українська
Українська  Português
Português  Français
Français  भारतीय
भारतीय  Türkçe
Türkçe  한국인
한국인  Italiano
Italiano  Indonesia
Indonesia  Polski
Polski Caching issues, incorrect content localization, or unexpected authorization errors are often related not to the application code, but to how HTTP headers are generated and processed during data exchange. These small yet critical elements of a request and response govern routing, security, compression, and even the language in which information is displayed. Understanding their purpose and proper configuration allows developers, testers, and administrators to avoid critical failures, optimize traffic, and improve the stability of web services.
When a browser sends a request to a website, it generates an HTTP request, which includes not only the URL pointing to the required resource but also a set of headers that describe how exactly the response should be handled. For example, when making an HTTP request to the YouTube domain, the structure will be as follows:
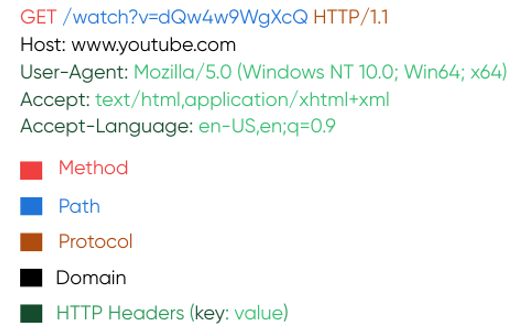
These do not contain the main payload (in this case — the video) but define the rules and processing context. This allows the server to make the correct decision about how to format the response: in what format, in what language, and with what compatibility.
The response to the above request will have a different structure and headers that transmit information such as date, time and time zone, server, video format, size, cache, and type of connection.
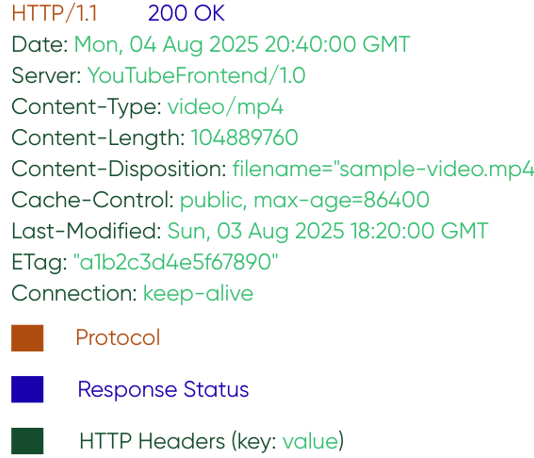
As seen from the example, an HTTP header consists of two parts: the name (key) and the value, separated by a colon. The name defines the type of information being transmitted, while the value specifies the actual content. Without them, client-server interaction would be unreliable and unstable.
In addition to request and response ones, there are also general purpose and entity headers. Each of them differs in its content and includes different types of messages.
These apply to both requests and responses, but they are not related to the content of the message body. Their inclusion is mandatory for all messages between client and server.
| Name (key) | Value |
|---|---|
| Cache-Control | Controls caching on the client or proxy side |
| Connection | Defines connection parameters, for example, whether it should be closed after completion |
| Date | Time and date |
| Pragma | Used for backward compatibility with HTTP/1.0 |
| Trailer | Indicates which headers will be added at the end of data transfer |
| Transfer-Encoding | Specifies the data encoding method, for example, chunked |
| Upgrade | Suggests switching to another version of the protocol, e.g., WebSocket |
| Via | Shows the chain of proxy servers through which the message has passed |
| Warning | Warnings related to caching or other aspects of data processing |
Contain information about the requested resource or the client initiating the request. Used exclusively in outgoing requests.
| Name (key) | Value |
|---|---|
| Accept | Defines acceptable media types that the client is ready to receive in response |
| Accept-Charset | Specifies acceptable character sets for the response |
| Accept-Encoding | Specifies acceptable compression schemes (e.g., gzip, deflate) |
| Accept-Language | Defines preferred response languages |
| Authorization | Contains the username and password encoded in base64 format, which transforms the data into a set of Latin letters, digits, and symbols for secure transfer |
| Cookie | Transfers data in the “name=value” format related to the current site |
| Expect | Indicates expected server behavior, e.g., 100-continue |
| From | Contains the email address of the request sender |
| Host | Defines the host and port of the target resource |
| If-Match | Makes the request conditional: executed only if the ETag matches |
| If-Modified-Since | Conditional request: if the resource has not changed since the specified date, status 304 Not Modified is returned |
| If-None-Match | Data processing is performed only if none of the transmitted ETags match the current one |
| If-Range | Used in partial resource requests: if not changed, the server returns the specified part |
| Max-Forwards | Limits the number of intermediate nodes (proxies) through which the request may pass (TRACE, OPTIONS) |
| Proxy-Authorization | Specifies authentication data for the proxy server |
| Range | Requests a specific byte range of data |
| Referer | Defines the source from which the user navigated to the site |
| TE | Specifies acceptable transfer extensions and encodings (e.g., trailers) |
| User-Agent | Contains information about the client software (browser, OS) |
Provide metadata about the server or the location of the returned resource. Applicable only to server responses.
| Name (key) | Value |
|---|---|
| Accept-Ranges | Indicates whether the server supports partial requests by ranges |
| Age | Shows the age of the response in seconds since its generation on the server |
| ETag | Provides a unique identifier of the site version (entity tag) |
| Location | Indicates an alternative URI for redirecting the client |
| Proxy-Authenticate | Used in 407 responses to specify the proxy authentication scheme |
| Retry-After | Displays the wait time before retrying the request (e.g., after a 503 response) |
| Server | Reports information about the server software |
| Set-Cookie | Sets cookies in the “name=value” format and supports parameters: Comment, Domain, Expires, Path, Secure |
| Vary | Specifies which headers are taken into account by the server when generating the resource representation |
| WWW-Authenticate | Used in 401 responses for client authentication |
Transmit information about the message body, such as its length, content type (MIME), and other metadata.
| Name (key) | Value |
|---|---|
| Allow | Lists HTTP methods supported by the resource |
| Content-Encoding | Indicates the encoding scheme applied to the body for the media type (e.g., gzip) |
| Content-Language | Defines the language used in the response body |
| Content-Length | Specifies the length of the response in bytes |
| Content-Location | Provides the actual location of the content if it differs |
| Content-MD5 | Provides an MD5 hash for verifying the integrity of the content |
| Content-Range | Specifies the data range when a portion of the entity is sent |
| Content-Type | Indicates the type of content and HTTP header format of the message body (e.g., text/html) |
| Expires | Sets the date and time after which the response is considered stale |
| Last-Modified | Shows the date and time of the last modification of the resource, according to the server version |
As previously discussed, there are different types of HTTP headers. Each of them plays its own role in the interaction process between the client and the server. Based on their purpose and scope, the main functions can be highlighted as follows:
They are not just technical attributes of the protocol but a full-fledged mechanism for fine-tuning client-server interaction. Proper configuration allows influencing routing, security, caching, transmission, and data interpretation. Depending on the goals and context of interaction, HTTP request headers can be applied in several practical scenarios.
They make it possible to form requests that are maximally close to the traffic of real users. Modifying the User-Agent allows altering the client’s digital fingerprint, while Forwarded and X-Forwarded-For provide routing and proxy management. Accept-Encoding and Accept-Language make it possible to request localized versions of resources according to predefined preferences. As a result, data can be safely extracted from web resources, ensuring a continuous process throughout the entire working session.
Many websites and services apply protection systems to prevent excessive or unauthorized activity. This may appear as limits on request frequency from one IP address, checks for specific HTTP headers, or content analysis. Proper configuration of Referer and Origin for specifying the source of a request, as well as Cookie and Authorization for confirming access rights, helps adapt interaction with resources under established conditions. If necessary, one can buy proxies, which distribute the load while accounting for regional specifics of operation, ensuring proper access and accuracy of data retrieval.
HTTP request headers help reduce the volume of transmitted data. For example, using Range and Accept-Ranges allows loading only the necessary fragments of a file, which is especially useful for resuming downloads of videos or large documents. If-Modified-Since and If-None-Match prevent the transfer of unchanged data by returning a 304 Not Modified code from the server. The use of Accept-Encoding: gzip allows receiving a compressed response and further reducing the volume of transmitted information. This approach lowers network load, speeds up processing, and helps optimize costs, which is especially relevant for large-scale queries and when working with paid APIs.
In secure systems, authorization and source verification headers work together but perform different functions. Authorization and Proxy-Authorization pass a token or access key to the target resource for confirming rights to work with a restricted API. If absent, the server responds with the WWW-Authenticate header specifying the supported authorization scheme. On the server side, Origin, Host, and Content-Security-Policy prevent request source spoofing. This set is used in systems with personal accounts, paid access, and administrative management.
In development and testing, HTTP headers are applied to simulate requests from different client types (User-Agent), check caching and analyze cache headers (Cache-Control, Expires), trace routes (Via, X-Request-ID), as well as reproduce errors in load and stress testing, assessing resilience and scalability of web applications.
You can view request or response ones in several ways: using the curl utility, Chrome DevTools, or specialized online services.
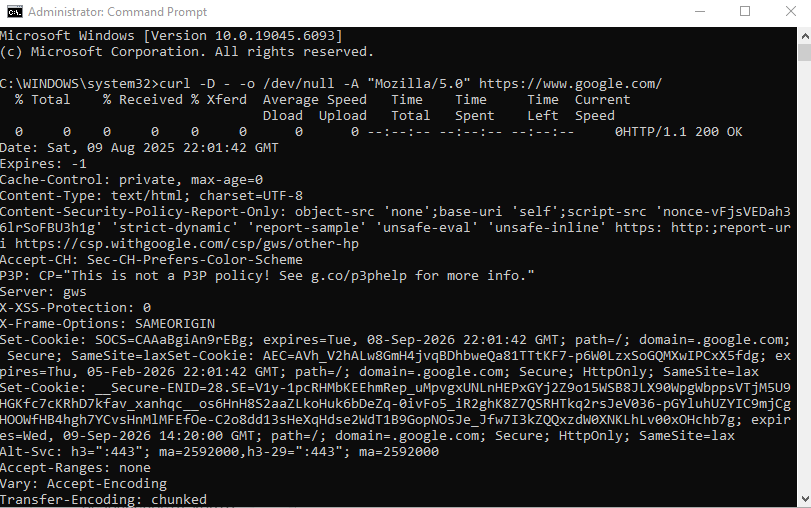
Enter the command:
curl -D - -o /dev/null -A "Mozilla/5.0" https://www.google.com/In Command Prompt, PowerShell, or Terminal, you can replace https://www.google.com/ with the address of any desired website to obtain its response headers.
Access through built-in developer tools in the Chrome browser or any other Chromium-based browser can be obtained by pressing F12 or through the browser menu: “More tools” → “Developer tools”.
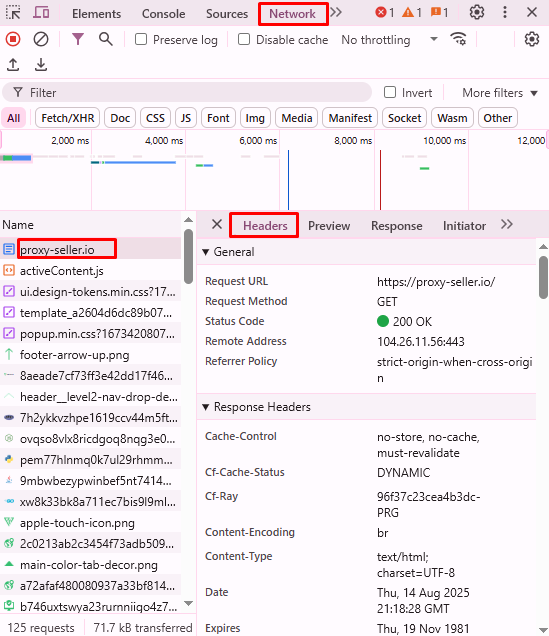
Go to the “Network” tab, then refresh the page with F5. In the right part of the window, all loaded elements will be displayed. In the “Name” column, select the required file, after which in the “Headers” tab the HTTP headers received in response to the request will be shown.
You can use the following resources:
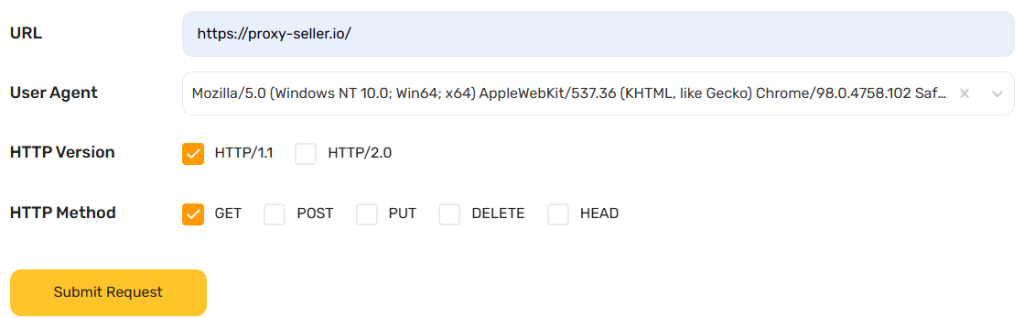
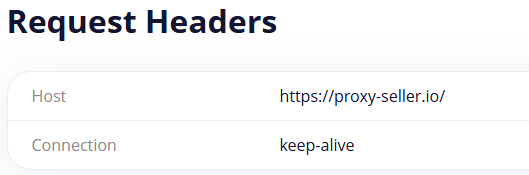
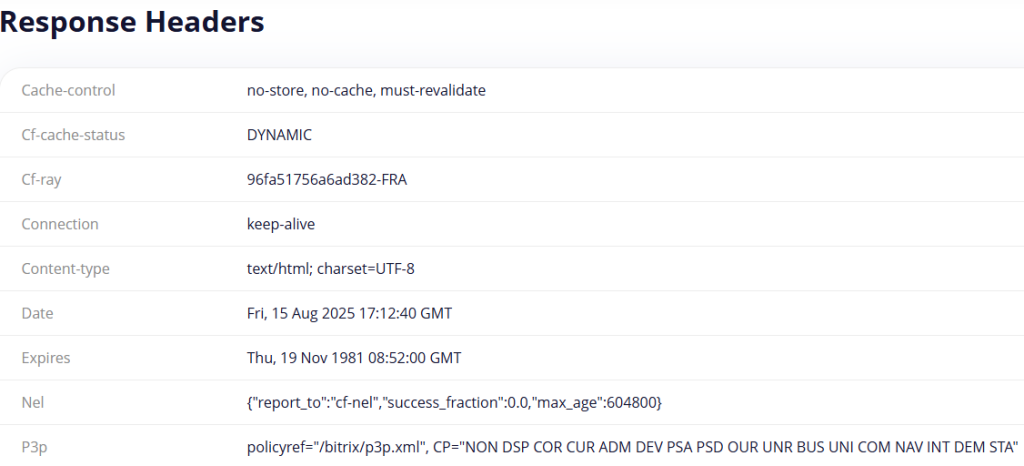
As an example, free.geonix.com/ru/http-headers is used. Its operation principle is simple: in the service's address bar, you need to insert the URL of the desired site, select “User Agent” and click “Send request”. A list of HTTP headers of the request and response received from the server will be returned.
Correct configuration plays an important role in ensuring stable and predictable system performance. Efficiency can be improved through three main approaches:
Regular checks of generated requests and analysis of transmitted headers help to promptly detect and eliminate such inconsistencies.
HTTP headers play a key role in data exchange between client and server. They help manage security, access, format, and volume of transmitted information, as well as influence the speed and stability of operations. They are actively used by developers, system administrators, security specialists, testers, and also web scraping professionals. A properly selected and consistent set of headers allows the system to function predictably, while users receive exactly the results they expect.
For effective work with HTTP requests, it is important to determine in advance which headers are critical for the project and configure them according to network characteristics, caching, localization, and routing. Regular inspection and updating of values helps avoid interpretation errors, reduce infrastructure load, and ensure the proper functioning of web services under different conditions.
In HTTP/1.x, header names are case-insensitive — the server and client treat them the same regardless of how they are written (for example, Content-Type and content-type are considered the same header). In HTTP/2 and above, they are transmitted only in lowercase, which simplifies processing and improves performance.
Yes, it is allowed to use custom ones for passing specific information, such as authentication or implementing custom logic. However, it is important to avoid conflicts with standard headers to ensure correct request processing.
Misconfiguration can lead to incorrect interpretation of the request by the server, which may result in failures, returned errors, or complete access blocking.
No. Only those necessary for a specific request should be specified. An excessive set of headers increases the volume of transmitted data, creates additional load on the network, and may slow down data processing.
Comments: 0