
 en
en  Español
Español  中國人
中國人  Tiếng Việt
Tiếng Việt  Deutsch
Deutsch  Українська
Українська  Português
Português  Français
Français  भारतीय
भारतीय  Türkçe
Türkçe  한국인
한국인  Italiano
Italiano  Indonesia
Indonesia  Polski
Polski Kameleo is a high-quality anti-detect browser that improves the privacy and security of a user's connection. It allows its users to manage multiple browsing accounts with different fingerprints, which makes it an effective solution for digital marketers, SEO experts, and other people who need to avoid being tracked online.
This article offers a guide on how to set up proxies on the Kameleo browser in order to provide a high level of efficient task resolving and make sure your digital information is safe.
Now, let's take a closer look at how to correctly configure a proxy in the Kameleo browser using the tutorial below.
The proxy integration starts by navigating to the tab labeled “Profiles” on the left side of the Kameleo browser interface. Make a click on “+ New” in order to create a new profile and subsequently modify the proxy you want to use.
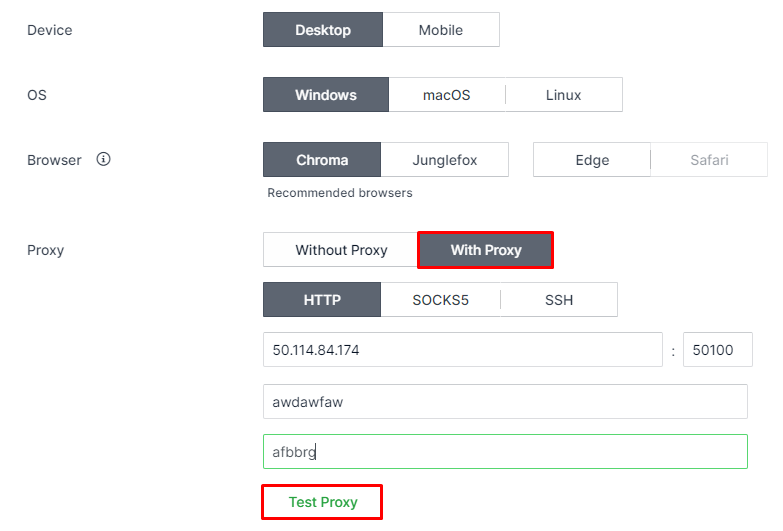
In the new window that has just opened, all the required information for the profile will be entered. Look for the “Proxy” section and switch from “Without Proxy” to “With Proxy”. Choose from the options provided what proxy protocol you want to use. Enter the IP address, port, and, if the proxy is a private one, the username and password. Finally, to check your proxy settings, you can click on “Test Proxy”.
Kameleo’s built-in checker will check the proxy server for any errors or operational issues. The outcomes, such as testing proxies for well-known websites’ availability and testing the geographical location of the proxy, will pop up in a separate window.

After the proxy settings have been successfully verified, complete profile configuration. The new profile will be available in the “Profile” tab and can be employed when needed.
For every person who wants to improve their privacy and additional setups of operation, a proxy server integrated with Kameleo would be a necessity – for all the reasons explaining the core idea behind a proxy. They hide your activity by masking the real IP address. Thus, preventing websites from tracking your activities and storing personal information.
Configuration of proxies within Kameleo supports the smooth operation of automation tools and bots, especially in scenarios where high-volume, automated tasks are necessary. Automated tools, when operated through a proxy are able to bypass common measures like rate limits or IP blocks, ensuring a constant engagement in providing service around the clock and accomplishing tasks such as data collection efficiently.
Also, proxies form a great addition to organizational security as they increase the attack surface area. Therefore, this makes it more difficult for an intruder to penetrate the defenses and exploit security loopholes targeted towards a specific IP. This is made possible by spreading the IP addresses used.
In essence, using a proxy with the Kameleo anti-detect browser not only fortifies your privacy but also expands your access capabilities, making it an essential setup for anyone leveraging the network for extensive and diverse online activities.
The appropriate proxy type to implement for Kameleo comes down to what your targets are:
There are also a few things to keep in mind when selecting the proxy protocol. For safe and secure web browsing and account authorization, Kameleo recommends the use of HTTP/S proxies, as they can manage encrypted traffic. However, SOCKS5 proxies are primarily used in large data transfers involving different types of traffic, for example, streaming, gaming or P2P applications. In Kameleo’s case, standard browsing should start with HTTP/S proxies, and more demanding ones are best with SOCKS5 proxies.
When setting up your Kameleo proxy, keep these tips in mind:
This practical approach prepares you for smooth proxy integration with Kameleo, ready for automated or manual browsing sessions.
You’ll automate browser tasks using Playwright connected to Kameleo proxy-enabled browser sessions.
To automate browsing, use:
To make your automation robust, handle errors and add retry logic for unstable network conditions or slow loading pages. This prevents your scripts from failing unexpectedly.
When your tasks are complete, properly close the Playwright session and stop the corresponding Kameleo profile to free system resources.
Here’s a practical list to keep your automation smooth:
Following these instructions lets you leverage Kameleo proxy with Playwright for efficient, stealthy web automation. Your proxy integration with Kameleo combined with Playwright’s control opens many automation possibilities.
The proxy settings in Kameleo need to be correctly configured so that the anti-detect browser can be fully utilized as a tool for privacy protection. Following the steps elaborately given above, users can make sure that they are utilizing the resources of Kameleo to the fullest. Always select the appropriate type of proxy server and monitor your settings to avoid any of the following technical issues.
Comments: 0