
 en
en  Español
Español  中國人
中國人  Tiếng Việt
Tiếng Việt  Deutsch
Deutsch  Українська
Українська  Português
Português  Français
Français  भारतीय
भारतीय  Türkçe
Türkçe  한국인
한국인  Italiano
Italiano  Indonesia
Indonesia  Polski
Polski Nmap is a tool that allows you to scan ports and perform many other network operations. The main uses of Nmap include:
Using a proxy server in conjunction with this tool allows you to hide the real IP address of the scanner, which significantly increases anonymity when performing port scanning. This is especially important when performing penetration testing or security research to avoid detection. Additionally, if the scanner's IP address is blocked by the target system or firewalls, using a proxy can bypass these restrictions by providing an alternative IP address to access the target host. For more stable sessions during security research, ISP proxies can be a practical choice because they tend to have a more consistent reputation than many datacenter ranges.
Integration of a proxy into the Nmap tool is facilitated using the ProxyChains program through specific commands. To set up this combination, follow these step-by-step instructions:
“sudo apt-get install proxychains”
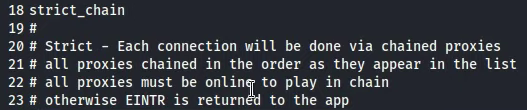
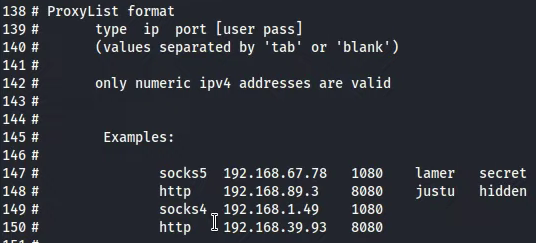
“sudo nano /etc/proxychains.conf”
![]()
“proxychains nmap -sT -p 80 example.com”
With these settings, the proxy setup is complete. This configuration will help hide your real IP address and circumvent any network restrictions of the target resource. It is advisable to buy private proxy access to ensure a high level of connection anonymization.
Comments: 0