
 en
en  Español
Español  中國人
中國人  Tiếng Việt
Tiếng Việt  Deutsch
Deutsch  Українська
Українська  Português
Português  Français
Français  भारतीय
भारतीय  Türkçe
Türkçe  한국인
한국인  Italiano
Italiano  Indonesia
Indonesia  Polski
Polski

Thanks to new web and cloud technologies, companies can function 24/7 with minimum expenses and no geographical limitations and automate and scale many processes all from a single browser. In this situation, Geelark offers a great solution for performing a myriad of tasks. In this article, we are going to examine the main features, technical specifications, proxy integration options, and pricing of such a tool.
This type of antidetect browser is designed to mask efforts that detect whether the request initiator is a human or a bot. It circumvents this limitation by replacing fingers with real user data, thus increasing success chances of anonymous logins.
Yet, it is insufficient to rely solely on spoofing fingerprints to mask one’s identity without being detected. Hence, the IP address, which guarantees anonymity, is extremely crucial.
The program permits the integration of proxy servers that make it possible to simulate a unique network connection for each individual account.
The mobile antidetect browser features one of the most distinctive technical implementations as well as a well-thought-out design. It is based on the open-source Chromium system, which permits the work to be done to incorporate additional measures for securing personal information and disguising multiple devices, primarily mobile phones. Every session is containerized, ensuring that each session remains mutually exclusive. Plus, cross-contamination of cookies, localStorage, and other elements from the client-side is prevented.
While most contemporary antidetect browsers are designed with desktop machines in mind and do not always cater for the emulation of cloud phone service or tablet usage, Geelark is unique in that every profile is designed as a cloud phone.
The software simulates mobile device operations, including:
While making a mobile profile, users need to provide specifications like the brand and model along with technical features. This is important to ensure the profile appears realistic to the security systems of the web and mobile applications.
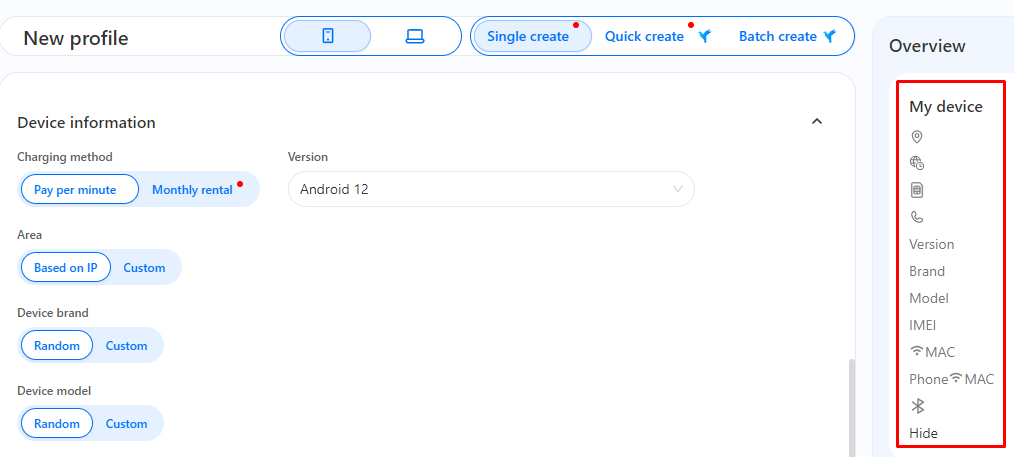
It has outstanding internal architecture as well as external parameter settings that help simulate mobile behavior.
A private proxy may be set up, or the profile may fall back to the default configuration. Proxy support for HTTP(S) and SOCKS5 and its integration with other components provide flexible traffic handling and fine-grained traffic setup. User anonymity, as well as working within restricted networks or corporate firewalls, becomes easy with these features. For instance, while utilizing Selenium for scraping Google Shopping, users are able to assign a distinct SOCKS5 proxy to every browser window. This allows multiple sessions to send requests through different IPs at the same time.
In addition to concealing the device’s IP address and utilizing other means of encryption, the tool further obfuscates a device’s fingerprint by modifying the User Agent, client headers, timezone, geolocation, hardware identifiers, and any other component that may be utilized by protection mechanisms to identify and block suspected users owing to automated behavior.
The benefits of Geelark are numerous, especially for multi-account operators, social media marketers, and traffic arbiters.
Core benefits of the system encompass:
The disadvantages include high network load when posting simultaneously from multiple accounts as well as no free version that functions beyond the profile creation cap.
It has minimal system requirements and is comparatively lightweight. Nonetheless, certain operating systems lack support. Ensure your platform version before proceeding to download it.
Supported are:
After confirming compatibility, grab the anti-detect browser from the official website that corresponds to your OS.
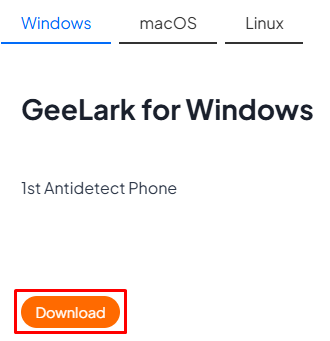
Select your preferred language version and download the .exe file. A slightly different than usual installation process will begin first by requiring Setup Wizard. Unlike most standard setups, registration or account login is required at the first step.
Account registration can be completed using an email address or phone number. This can be switched by toggling the appropriately labeled button in the upper right corner of the screen.
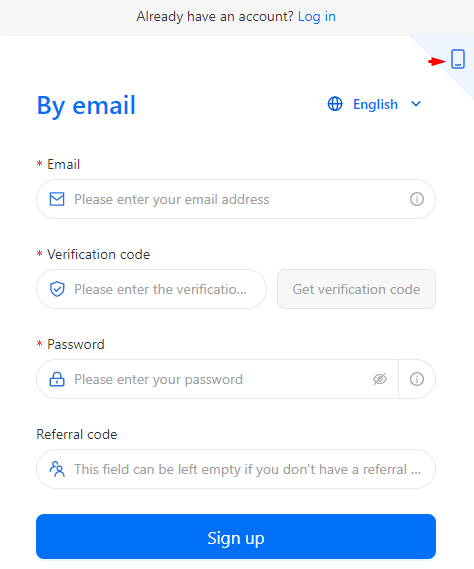
The registration step requires solving a CAPTCHA challenge and submitting a verification code. Right after that, you are able to immediately design a profile that you wish to set up.
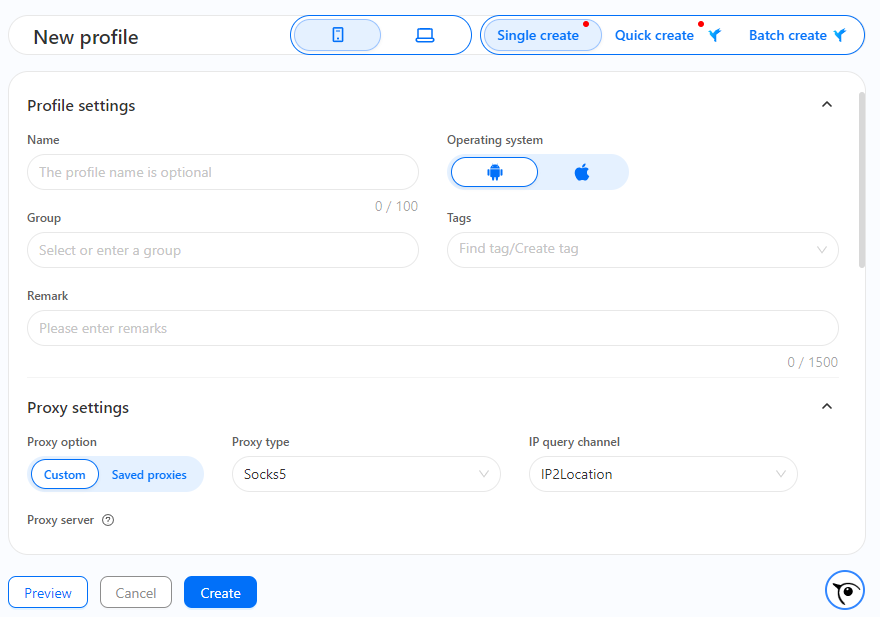
During the account registration, it is possible to set up the device type (phone or PC), the operating system type (Android/iPhone or Windows/macOS), specify a private proxy, and select the geolocation. When emulating a PC, you can set up the browser and its version that can be used for automation or cross-browser testing.
Its pricing is adaptable and meant for all types of usage, from individuals to bigger teams and companies. It can be charged either based on the minute or via a 30-day subscription. The use of additional features, cloud phone, and the base fee are all charged separately.
Currently offered:
| Features | Free | Base | Pro | Custom |
|---|---|---|---|---|
| Cost | 0 | from $5/month | from $19/month | Based on client's needs |
| Free minutes | 30 | from 60 | from 60 | Customized |
| Mobile profiles | 2 | from 5 | from 20 | Customized |
| Browser profiles | 0 | 1000 | From 1000 to 10 000 | Customized |
| Teamwork | – | + | + | + |
| Task automation | – | + | + | + |
| Analytics | – | – | + | + |
| Synchronizer | – | – | + | + |
| AI editor | – | – | + | + |
| Bulk profile creation | – | – | + | + |
Note that the free minutes are those that come with the selected plan. Specific features, such as using certain Android versions, come at an added cost.
With this pricing model of browser, one might question purchasing it. Investing with this tool can be justified fully, especially for focused projects centered on automation and scalability.
To begin with, the tool does provide an easy entry point with some of the lowest price ranges, which is a great option for small teams and startups.
The platform allows integration with mobile apps, which is most useful for businesses dealing with TikTok, Reels, YouTube Shorts, and other short videos. It also comes with a built-in AI video and graphics editor, which allows users to create unique visual content.
Moreover, the platform provides team collaboration in paid plans and facilitates further participation by enabling the adding of other users on the account, assigning roles, and managing tasks from a single focal point.
The tool was explicitly crafted to guarantee sophisticated multi-accounting from the web and mobile. Nevertheless, due to its extensive capabilities, it is now widely used in traffic arbitrage, e-commerce, SMM, and many others that value flexibility, automation, control, and anonymity. Now let us examine the highlights of its features.
A user that wants to increase their account rank (e.g., TikTok, Instagram, YouTube Shorts, Facebook, X, Reddit, Pinterest, Vinted, Gmail, Telegram, Tinder, and Venmo), will need to execute a lot of monotonous tasks like:
However, Geelark’s isolated environments, proxy controls, and anti-detection tech tackle challenges like account bans, frequent CAPTCHA, and strict IP restrictions head-on.
Here’s a quick look at specific automation tools and their uses:
| Platform | Automation Tool Use |
|---|---|
| TikTok | Schedule posts, auto-like videos, auto-reply comments. |
| Instagram Reels | Automate story posts, engage followers automatically. |
| YouTube Shorts | Upload videos, manage comments. |
| Plan posts, automate upvotes/downvotes. | |
| Create pins, manage boards. |
An example of an automation scenario, such as for bulk publishing of content, can be outlined as follows:
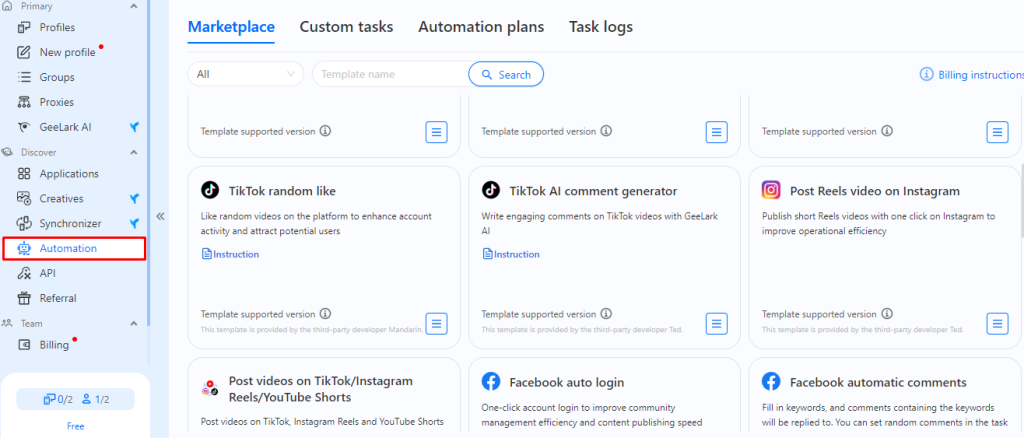
The automation system allows synchronous execution of actions performed on one user account to be duplicated on different users' accounts, which is useful in the case of dozens of identical profiles or when running large-scale advertising campaigns.
Content can be executed simultaneously across hundreds of accounts within seconds. It is also possible to review the operational history as well as the publication effectiveness – for example, on product pages of Shein, track audience engagement or product popularity.
Multi-account management is simple. You can run several virtual phones simultaneously with fully separate data silos. This means you can log into different social accounts or platforms without the risk of cookies or sessions mixing. It solves common problems, such as account bans caused by cross-account contamination or fingerprint overlap.
Privacy and security get a boost from Geelark’s anti-detect technology. It masks device fingerprints by randomizing hardware IDs, browser fingerprints, and operating system details. This technology prevents platforms from detecting multiple accounts or fake devices. Combined with environment masking, it helps avoid CAPTCHA, IP blocks, and account suspensions.
Geelark is one of the best phone emulator tools on the market because it comes with built-in artificial intelligence tools tailored for generating and editing creatives. With these tools, users are able to perform background modifications, apply sounds, add filters, and adjust other parameters for videos, making them easier to edit.
Moreover, text along with post titles can be generated automatically so that caption duplication across platforms will not be detected. This function proves to be particularly handy whenever you want to post in bulk on TikTok, Facebook, Instagram, and other similar platforms.
Some people online state that this tool is a phone emulator, which is only partially true. It is a mobile antidetect browser with cloud-based emulation of mobile device features.
As a profile is created, it connects to a remote server, which retrieves data of a real device, such as:
This is highly convenient because traditional emulators have a cloud-based solution that is lightweight, fast, and doesn’t require additional disk space, RAM, or CPU resources, in comparison to other desktop computers or laptops where a significant amount of power is consumed.
In addition, when using standard emulators, like Bluestacks, you are usually limited to only one virtual phone. With Geelark, Android and iPhone devices can be generated as a whole farm and seamlessly operate without attracting attention from monitoring anti-bot systems.
By going to the Profile section, one can create a cloud phone by choosing the brand, model, Android version, and geolocation down to the exact city.
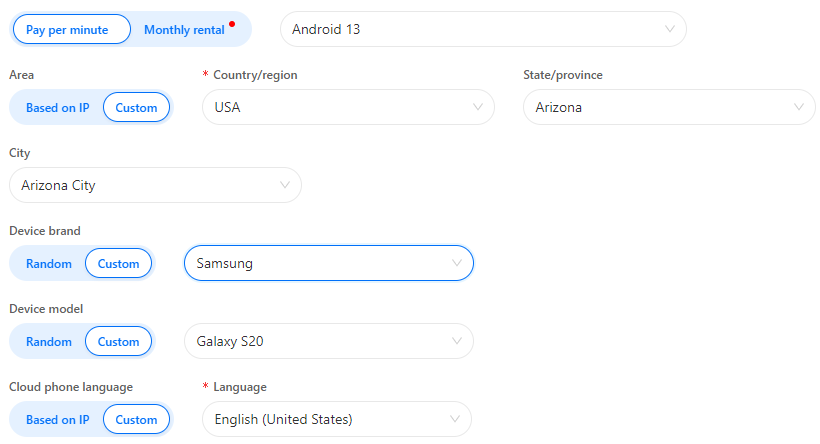
Once the account is set up, applications can be installed from the internal catalog.

In case a certain application is missing, you can install it onto the cloud phone by uploading an APK file manually.
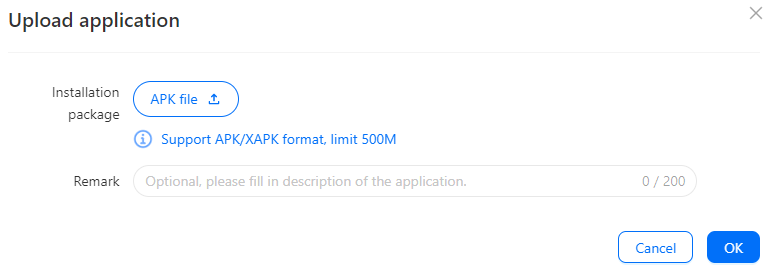
For this reason, Geelark is not only an antidetect browser but also serves as a mobile emulator capable of running a variety of applications and installing APK files, thereby providing invaluable utility for mobile platform specialists.
Given that such a browser simulates the functioning of a mobile handset, it can be utilized not only for managing on-hand accounts but also for cloud IP telephony.
This is especially useful for the support of clients where the interaction requires the verification of mobile numbers via SMS or calls. Even though cloud telephony is not a feature provided by Geelark, he does allow the use of third-party services such as Zadarma, OnlinePBX, Sipuni, among others, with the capability of making each profile function as a self-sufficient mobile phone.
Setting up a proxy in this browser is simple – just follow these steps:
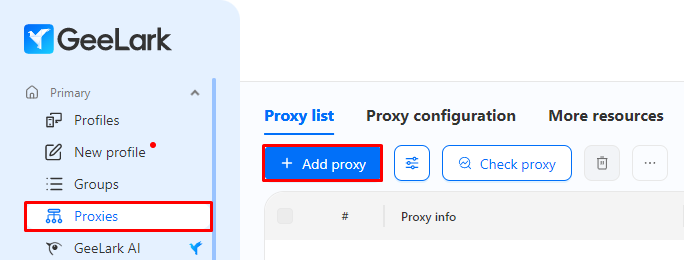
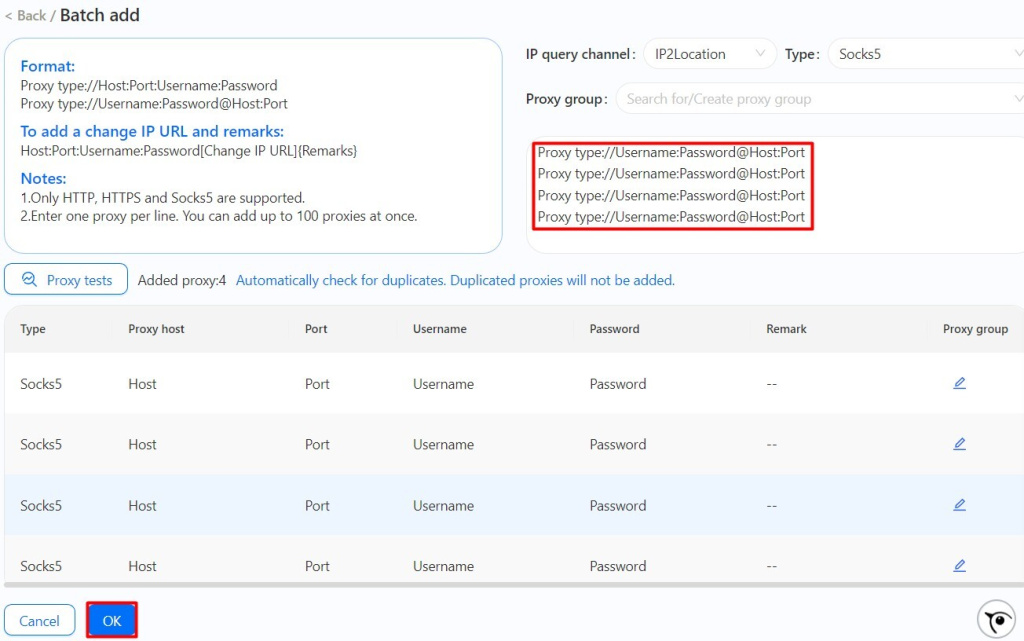
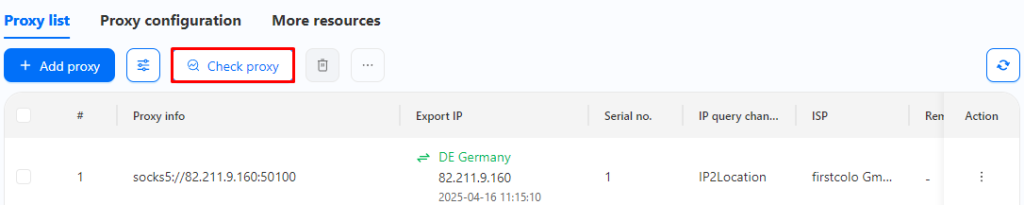
Proxy settings can also be modified when creating a new profile or while modifying an old one, by heading to section “Proxy” and filling the necessary configurations in designated text boxes.
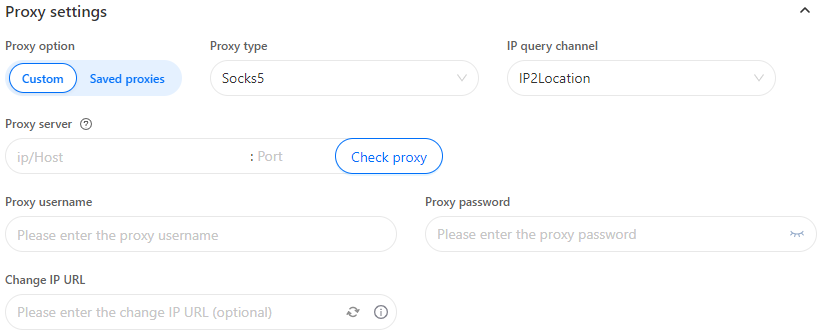
With this, one can easily conclude that the configuration of proxy servers in Geelark is straightforward. Altering the IP address increases anonymity since it creates a new and distinct environment for every account. When coupled with device fingerprint spoofing, it maximizes realism while minimizing detection.
You'll learn how to leverage Geelark Cloud Phone in real-world tasks.
The core features – multi-account management, proxy integration, automation suites, and strong security – directly support these use cases, saving time and increasing success rates.
Geelark’s antidetect technology works by spoofing device fingerprints and randomizing hardware IDs like MAC addresses, IMEI, and device models. It emulates OS and browser environments accurately, preventing websites from tracking or detecting multiple accounts or bots. This stops platforms from linking activities to the same source.
Proxy integration is fully embedded. You can choose between shared or dedicated proxies, set up automatic proxy rotation, and even chain proxies for extra layers of anonymity. You control geolocation IPs to match your target audience or platform requirements.
Geelark supports HTTP/S and SOCKS5 proxies with flexible rotation and custom proxy list options. Integration is built into the platform for seamless switching and assignment. Proxies are essential for anonymizing traffic and spoofing geo-locations.
Proxy-Seller powers Geelark’s proxy needs by offering SOCKS5, HTTP(S), IPv4, IPv6, residential, ISP, and mobile proxies. Their network spans 220+ countries, ensuring diverse and fast IPs to reduce bans and blocks.
Proxy-Seller offers practical benefits such as 24/7 support, an easy-to-use dashboard, API access, and flexible rental plans. This integration ensures stable proxy management built right into your Geelark workflow.
Proxy-Seller enhances this setup with high-end proxy features: unlimited bandwidth up to 1 Gbps, username/password or IP whitelist authentication, and a large network covering over 800 subnets across 400+ networks. Their proxies come from ethically sourced IPs, comply with GDPR, CCPA, ISO/IEC 27001, and the ePrivacy Directive, and include partnerships with ISPs and mobile carriers to ensure reliability and privacy.
Proxy-Seller’s API lets you automate proxy management and scale deployments within Geelark workflows, making your proxy usage efficient and flexible.
The Geelark review shows that it is not only a mobile antidetect tool but evidently is well structured and designed for ease for users prioritizing multi-account management to dish out effective control, layered anonymity, security, and efficiency. It lets every profile wield a unique environment digitally, like a separate IP address and fingerprint, reducing the odds of detection greatly.
Comments: 0