
 en
en  Español
Español  中國人
中國人  Tiếng Việt
Tiếng Việt  Deutsch
Deutsch  Українська
Українська  Português
Português  Français
Français  भारतीय
भारतीय  Türkçe
Türkçe  한국인
한국인  Italiano
Italiano  Indonesia
Indonesia  Polski
Polski All devices acting as proxy servers are integrated into a single network. To facilitate efficient interaction among these devices, they are segmented into distinct groups known as proxy server subnets. Each subnet consists of a common range of IP addresses, and importantly, all subnets are isolated from one another. This segmentation is crucial for traffic control, performance optimization, and simplifying network management for administrators. Given this architecture, we will next explore the fundamentals and principles of subnets, as well as their impact on the functionality of proxy servers.
Based on how subnets are utilized on the Internet, there are two primary types: public and private. The choice between them depends on the user's objectives.
Public subnets are open for communication with all other networks on the Internet. These subnets typically host web servers, mail servers, cloud services, and other resources that require external access.
Private subnets, on the other hand, are either not accessible from the Internet or have limited accessibility based on their configuration. They are commonly employed within corporate networks to control access and enhance security for data exchanges between devices on the network. Private subnets are designed to connect specific computers, ensuring data confidentiality and eliminating exposure to "neighbors" within the subnet.
The setup of a private subnet often involves cloud services such as Microsoft Azure or Google Cloud Platform (GCP), alongside various network hardware like routers, firewalls, and network management devices.
It's crucial to recognize that the type of subnet also plays a significant role when using proxy servers. Typically, purchasing a proxy server provides the user with an IP address from a public network, allowing unrestricted access to various web resources. Conversely, proxy servers operating from private subnets may have restricted Internet communication, which is why they are specifically configured within corporate networks for particular tasks.
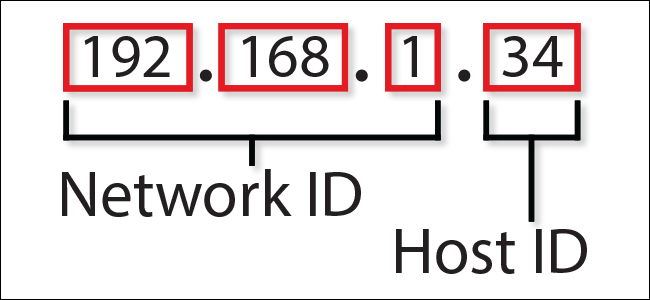
To gain a deeper understanding of subnets, it is essential to learn about the concept of a proxy server subnet mask. An IP address is divided into two parts: the network address, which is common to all devices on that network, and the host address, which identifies a specific device within that network. The subnet mask is a parameter that specifies which part of the IP address represents the network and which part represents the host. This distinction is crucial for devices to determine the correct recipient of data within the network.
The subnet mask is typically expressed in dot-decimal notation, which consists of four blocks of numbers separated by dots, such as 255.255.255.0. When this mask is applied to an IP address, the numbers preceding the zeros in the mask define the subnet, and the zeros designate the host portion. Thus, for IP addresses within the same subnet, the first three blocks of numbers will remain constant, and only the last block will vary, distinguishing one host from another. An example of how this subnet structure looks can be seen in the diagram below:
Understanding what a subnet mask is and its purpose simplifies the process of identifying a subnet. To do this, you need to know your IP address and your subnet mask. Let's explore how you can retrieve this information across different operating systems.
On Windows, you can obtain your IP address and subnet mask by following these steps:
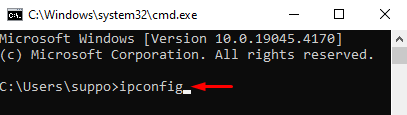
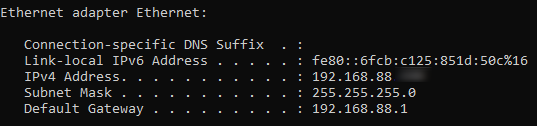
In the example provided in the screenshot, the subnet is identified as 192.168.0. The number in the last block is what differentiates individual devices on the network, representing the specific computer’s address within that subnet.
To check the subnet mask on an Apple device through the system settings, follow these steps:
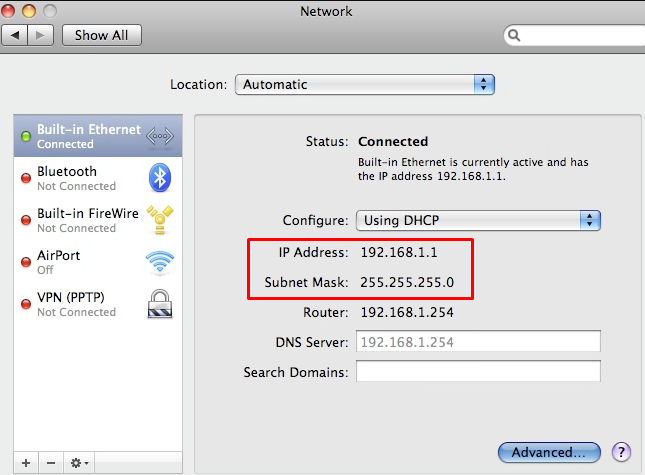
For example, if the subnet mask shown in the screenshot is the standard 255.255.255.0, then the subnet number would be 192.168.1.
In the Linux operating system, you can determine the subnet mask and IP address using the terminal by following these steps:
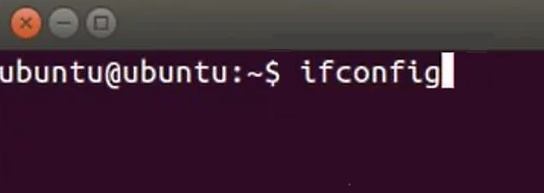
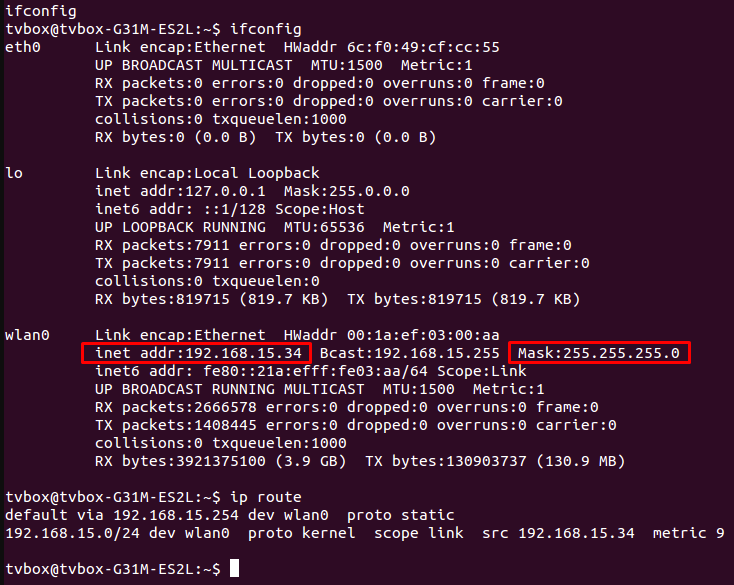
It's important to understand that this method only checks the subnet mask of the native IP address of the user's computer. You cannot calculate a subnet mask from an IP address using online checkers, nor can you initially obtain a proxy with a known subnet mask. Therefore, users should verify this information with their proxy provider or consider the first three blocks of numbers in the IP address list when purchasing a proxy. If they match, then all addresses belong to the same subnet, which could potentially influence the operation of the proxy server.
Grouping IP addresses into the same subnet can lead to both advantageous and detrimental outcomes. Here are the benefits of organizing IP addresses into subnets:
There are additional ways in which subnets impact proxies, particularly related to user activities on IP addresses within the same subnet and how web security systems respond.
When a security system detects suspicious activities, such as spamming or excessive request sending from an IP address, it may impose restrictions or blocks on that specific IP or potentially the entire subnet. The possible adverse outcomes for users of proxy servers in such scenarios include:
Additionally, regional restrictions may be applied to subnets. If a subnet is associated with a specific geographical location, this can restrict access to certain resources for the IP addresses within that subnet, which adversely affects the ability to bypass blocks and filters.
Problems may also emerge from the activities of an individual user or other users sharing the same subnet. Generally, web resources are cautious about implementing drastic measures such as blocking, to avoid negatively impacting users who have not engaged in any prohibited actions. However, certain types of sites, such as bookmakers, might impose blocks more frequently. This is because clients of these services often use a pool of IP addresses from the same subnet to engage in activities that contravene the site's policies.
The concerns raised above prompt users to question how they can maintain their isolation and anonymity when using an IP address from a common subnet. There are various methods to prevent specific IP addresses from being associated with activities on a subnet, and the choice of method will depend on the type of proxy needed. Here are the four main types of proxy servers:
Next, we will explore the primary strategies to shield your IP addresses from the effects associated with the subnet, focusing on the different types of proxies available.
When purchasing several datacenter or ISP proxy servers, a user may end up with IP addresses from the same subnet, as these IPs are static and part of a specific network infrastructure. Consequently, if a web resource decides to block the entire subnet, all of the user's IP addresses could become inoperable. To avoid this, it is crucial to effectively utilize proxy subnets by selecting IP addresses from different subnets. This approach is particularly important when purchasing a pool of IP addresses and can be implemented in the following ways:
Using IP addresses from different subnets is advantageous for activities such as web scraping, multi-accounting, and e-commerce operations. In these cases, ISP proxies are generally more favorable than IPv4 and IPv6 proxies, as they are associated with internet providers and are less frequently blocked by web resources. However, for short-term tasks where cost is a concern, data center proxies might be a suitable choice since they are the most economical option.
For certain applications, employing private subnets is an appropriate option. These are configured using dedicated hardware and a subnet mask, which specifies the maximum number of computers that can connect. Private subnets are particularly relevant for corporations and enterprises of various sizes, enabling secure data exchanges within specific departments, offices, or branches.
Integrating proxy servers in this scenario allows organizations to enhance control over employee access to web resources and to manage traffic more effectively. However, locating a proxy server that operates within a private subnet can be challenging. One solution is to establish your proxy server, provided there is access to a private subnet.
Moreover, compared to the use of public proxy servers, this method is more complex and generally suitable for organizations that possess the necessary financial resources for implementation. For individual users with personal proxy needs, this approach might not be feasible. For such users, exploring other proxy solutions would be more beneficial.
When selecting residential or mobile proxies, the specific subnet they belong to is generally irrelevant due to the dynamic nature of these IP addresses. Both types of IP addresses change periodically, which can be configured based on user preferences.
When opting for residential proxies, users can specify several parameters to tailor the service to their needs, including:
Based on these choices, the proxy provider will issue a pool of IP addresses from computers that are actively distributing traffic at the time of the user's request. The pricing model for residential proxies is typically based on the amount of traffic used rather than the number of IP addresses, as these proxies are associated with real users' connections that regularly rotate IP addresses. This frequent change in IP addresses means they are rarely blocked, making the specific subnet of lesser importance.
For mobile proxies, the selection process allows users to choose:
Upon purchasing a mobile proxy, users establish the principles and timing for IP address changes. They are then assigned an IP address from the mobile operator's pool, which rotates according to the predefined settings. Due to the unique architecture of mobile networks, mobile IP addresses are seldom blocked, negating the need for users to concern themselves with the subnets these IPs belong to. This flexibility makes mobile proxies particularly useful for users requiring reliable and uninterrupted access to the internet without the typical constraints associated with fixed IP addresses.
These types of proxy servers are highly favored by users seeking to circumvent blockages and restrictions associated with proxy server subnets, making them an ideal choice for various applications, including:
In conclusion, it's important to recognize that subnets are a key factor influencing the functionality and reliability of proxy servers, particularly affecting IPv4 and IPv6 data center proxies. The tendency of web resources to block an entire subnet in response to suspicious or malicious activity from even a single IP address within that subnet is a significant vulnerability. In contrast, mobile and residential proxies are generally accorded a higher level of trust by web resource security systems due to their dynamic nature and different operational principles. Consequently, for critical applications, users are advised to focus not just on subnets but on the type of proxy they are selecting. Making informed choices based on the specific goals of their activities can greatly enhance the effectiveness of the proxy server.
Comments: 0