
 en
en  Español
Español  中國人
中國人  Tiếng Việt
Tiếng Việt  Deutsch
Deutsch  Українська
Українська  Português
Português  Français
Français  भारतीय
भारतीय  Türkçe
Türkçe  한국인
한국인  Italiano
Italiano  Indonesia
Indonesia  Polski
Polski There are numerous resources available for automatically checking the functionality of proxies. Online checkers are among the easiest to use, offering significant time savings. The verification process can be particularly time-consuming when installing and operating specialized software and programs, especially when a large number of proxies need to be checked. But this guide will explain the function of a proxy checker, detail how the mechanism operates, and cover the key features you should look for to select an efficient tool for your needs.
A proxy checker is a tool designed to verify the validity and performance of proxy servers, along with determining additional characteristics. Its primary function is to ensure that the proxies being used are operational and capable of delivering the needed functionality.
Validating the effectiveness of a proxy is crucial when preparing to use proxies and web resources, as non-functional proxy servers can significantly impede work or even prevent the completion of tasks. Employing a proxy checker enhances the safety and efficiency of user interactions with online resources and helps in selecting the most appropriate servers for specific needs.
You’ll learn how testing proxies impacts your workflow and online security.
Here’s a practical checklist to avoid these risks:
Real cases show companies losing access to services due to proxy failures, leading to lost revenue and damaged operations. Using a reliable proxy checker online or a SOCKS proxy checker helps you identify these issues early and maintain a smooth workflow.
You’ll learn how to evaluate proxies systematically for best performance.
Practical Benchmarks:
Here’s a practical list for evaluating proxies:
Proxy-Seller stands out by offering a wide proxy range: residential, ISP, datacenter IPv4/IPv6, and mobile proxies. They deliver reliable speeds up to 1 Gbps and 99% uptime. Proxy-Seller supports both SOCKS5 and HTTP(S) protocols.
Their user-friendly dashboard lets you auto-renew, switch proxy types with ease, and automate management through API. With proxies available in over 220 countries, you get precise geolocation targeting. Authentication options include username/password and IP whitelist, matching diverse security needs.
Most importantly, Proxy-Seller proxies maintain high anonymity levels, making them ideal for sensitive workflows.
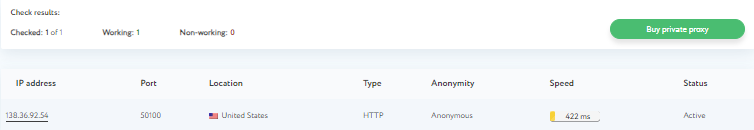
An online proxy checker enables users to analyze and verify a list of proxy servers based on various criteria such as availability, location, degree of anonymity, and protocol type. It provides detailed reports about each proxy, helping users assess which ones best meet their specific requirements.
The operating principle of an online proxy checker involves sending requests through each proxy from a user-uploaded list of IP addresses and analyzing the responses received. This process helps verify the functionality and suitability of the proxy servers. Here are the key aspects that the checker evaluates:
Additionally, some proxy checkers can detect incorrect proxy performance, including slow response times, frequent errors, or suspicious headers. These issues might indicate potential problems with the proxy server that could compromise privacy and lead to the leakage of users' personal data. This comprehensive analysis helps users select the most reliable and efficient proxies for their needs.
The validity of a proxy is crucial for maintaining network security and ensuring the effective online activity of users. Here are the key aspects in which proxy validation plays a vital role:
Over time, the characteristics of proxy servers can change. A proxy that was once functional and offered anonymity might become accessible or transparent, leading to potential risks such as data leaks, traffic interception, and account blocking. Regularly checking proxies ensures that users continue to employ reliable and secure proxies, safeguarding their online activities.
You can check the validity of your proxy list online using our «Proxy checker» tool. This tool provides a quick and free way to obtain information about the availability, location, speed, and protocol type of proxy servers, facilitating their effective use and integration into your software. Our checker can validate various types of proxies, including server, mobile, and residential proxies, with the capability to check up to 100 proxies at a time.
To get started with an online proxy checker tool, here are the steps you should follow:
You’ll learn why checking IP reputation is vital to avoid risky proxies. Proxy IPs with a history of abuse or spam can cause blocks, bans, or poor performance.
Here’s a straightforward list to manage reputation checks effectively:
You can integrate these checks into your proxy checker online or SOCKS proxy checker workflow to maintain a clean, trustworthy proxy pool that keeps your operations smooth and safe.
Using an automated online proxy checker will assist users in verifying the validity of their proxy servers and analyzing them based on various criteria. This ensures efficient setup and secure interaction with web resources, as using reliable proxies encrypts your traffic and protects personal data from potential leaks.
Comments: 0