
 en
en  Español
Español  中國人
中國人  Tiếng Việt
Tiếng Việt  Deutsch
Deutsch  Українська
Українська  Português
Português  Français
Français  भारतीय
भारतीय  Türkçe
Türkçe  한국인
한국인  Italiano
Italiano  Indonesia
Indonesia  Polski
Polski On January 28, 2026, Google's Threat Intelligence Group disrupted one of the largest residential proxy networks ever discovered. The operation targeted IPIDEA – a backend infrastructure that secretly powered at least 13 different proxy and VPN brands.
If you've been using any of the following services, your proxy infrastructure is now compromised:
|
Provider |
Status |
|---|---|
|
922 Proxy |
⛔ Disrupted |
|
LunaProxy |
⛔ Disrupted |
|
PyProxy |
⛔ Disrupted |
|
IP2World |
⛔ Disrupted |
|
PIA S5 Proxy |
⛔ Disrupted |
|
360Proxy |
⛔ Disrupted |
|
ABC Proxy |
⛔ Disrupted |
|
Cherry Proxy |
⛔ Disrupted |
|
Tab Proxy |
⛔ Disrupted |
|
Provider |
Status |
|---|---|
|
Galleon VPN |
⛔ Disrupted |
|
Radish VPN |
⛔ Disrupted |
|
Door VPN |
⛔ Disrupted |
|
Component |
Impact |
|---|---|
|
LumiApps SDK |
Removed from 600+ Android apps |
|
Asocks |
Infrastructure disrupted |
Need to switch immediately?
Talk to Sales about migration → Get a custom migration plan with special conditions for affected customers.
Google's Threat Intelligence Group, in collaboration with law enforcement, executed a coordinated takedown of the IPIDEA residential proxy network. Here's what they found:
|
Date |
Event |
|---|---|
|
2019-2020 |
IPIDEA begins operating, builds residential proxy network through SDK partnerships |
|
2021-2023 |
Multiple proxy brands launch using IPIDEA infrastructure (922, Luna, PyProxy, etc.) |
|
Early 2025 |
Google Threat Intelligence begins investigation after detecting botnet-like traffic patterns |
|
Q4 2025 |
Law enforcement coordination begins across multiple jurisdictions |
|
Jan 28, 2026 |
Google executes coordinated takedown, disrupts C2 infrastructure |
|
Jan 29-30, 2026 |
Affected providers experience widespread outages, customer complaints surge |
|
Feb 2026 |
Industry-wide scrutiny of residential proxy sourcing practices |
Understanding what went wrong helps you evaluate providers more carefully.
The Problem with IPIDEA's Approach:
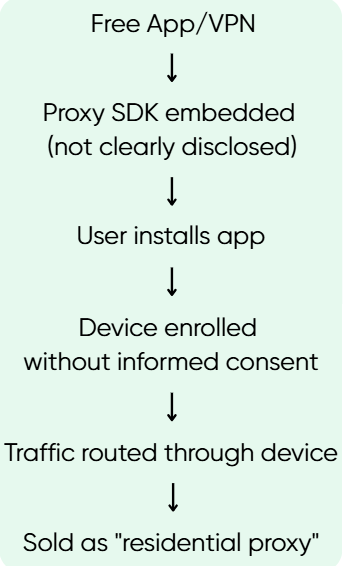
The issue wasn't SDK-based proxy networks in general – it was how IPIDEA operated: users installing a flashlight app or free VPN had no clear understanding their device would become a proxy exit node.
The investigation revealed that IPIDEA wasn't just a proxy network – it was infrastructure for cybercrime:
"While some providers may indeed behave ethically and only enroll devices with the clear consent of consumers, any claims of 'ethical sourcing' must be backed by transparent, auditable proof of user consent."
If you were using any of the affected providers, you face several immediate risks:
Your data collection, ad verification, or price monitoring workflows are now broken. The IP pools you relied on no longer exist or are severely degraded.
If your company has compliance requirements (SOC 2, GDPR, internal policies), you may have unknowingly used infrastructure linked to criminal activity. This creates audit and liability concerns.
Traffic routed through compromised infrastructure may have been intercepted, logged, or manipulated. Consider what data passed through these proxies.
This is exactly the scenario that procurement and security teams worry about. Your vendor's vendor turned out to be problematic.
The IPIDEA shutdown is a wake-up call for the entire industry. Here's how to evaluate providers going forward:
|
Question |
Good Answer |
Red Flag |
|---|---|---|
|
How do you source residential IPs? |
Clear explanation of partnerships and consent model |
"Proprietary" or vague answers |
|
Do users know their device is a proxy? |
Yes, with clear disclosure |
"It's in the terms of service" |
|
How do you prevent abuse? |
Specific controls, AUP enforcement |
No clear policy |
|
Can you provide compliance documentation? |
Yes, DPA/security docs available |
Resistance or delays |
We understand you need to move fast. Here's why Proxy-Seller is a safe choice:
Proxy-Seller has been operating since 2014 – long before SDK-based residential proxy models existed. Our infrastructure and sourcing methods predate and are completely independent from IPIDEA and similar networks.
We were not affected by the January 2026 disruption. Our residential IP pool uses a fundamentally different sourcing model that does not rely on:
Our residential IPs come from:
We serve enterprise customers who require:
|
Product |
Use Cases |
Key Features |
|---|---|---|
|
Residential Proxies |
Ad verification, price monitoring, market research |
195+ countries, sticky sessions, real user IPs |
|
ISP Proxies |
SEO monitoring, SERP tracking, social media |
Static residential IPs, unlimited bandwidth |
|
Mobile Proxies |
App testing, mobile ad verification |
Real 4G/5G carrier IPs, geo-targeted |
|
Datacenter IPv4/IPv6 Proxies |
High-speed scraping, bulk operations |
Dedicated IPs, maximum performance |
We know switching providers is disruptive. To make your transition easier, we're offering affected users a special migration package:
Contact Sales - enterprise@proxy-seller.com
Mention you're migrating from an affected provider to get special conditions.
If you were using 922 Proxy, LunaProxy, PyProxy, IP2World, PIA S5 Proxy, 360Proxy, ABC Proxy, Cherry Proxy, Tab Proxy, or the associated VPN services (Galleon, Radish, Door VPN), your provider was part of the IPIDEA network that was disrupted.
How to check if a provider not on this list was affected:
Traffic routed through compromised infrastructure could potentially have been logged or observed by malicious actors who also used the network.
Assess your risk level:
|
What you sent through proxy |
Risk |
Action |
|---|---|---|
|
Read-only public data scraping |
Low |
Continue normally with new provider |
|
Login credentials |
High |
Change passwords immediately |
|
API keys / tokens |
High |
Regenerate all keys |
|
Payment information |
Critical |
Monitor accounts, consider card replacement |
|
Internal company URLs |
Medium | Review access logs, consider URL changes |
Most customers can migrate within 24-48 hours. Our API format is similar to most providers, requiring minimal code changes. Our support team can assist with the transition.
Typical migration timeline:
Success rates depend on many factors: target sites, request patterns, geographic needs. We recommend:
Many customers report improved success rates due to our pool quality, but your results depend on your specific use case.
Unfortunately, this is between you and that provider. We cannot honor balances from other services. However, we offer special conditions for customers migrating from affected providers – contact our sales team to discuss.
To pursue recovery from your old provider:
Yes, but with appropriate diligence. The issue wasn't residential proxies as a category – it was a specific sourcing model (SDK-based enrollment without real consent).
Trustworthy residential proxy characteristics:
Key points for internal communication:
We can provide documentation to support your internal review - contact enterprise@proxy-seller.com
|
Type |
Best For | IP Source | Session Length |
|---|---|---|---|
|
Residential |
Protected sites, anti-bot bypass | Real home internet users (opt-in) | Rotating or sticky (up to 30 min) |
|
ISP (Static Residential) |
Long sessions, account management | ISP partnerships, static assignment | Unlimited (same IP) |
|
Mobile |
Mobile-specific verification, social | Real mobile carriers | Rotating or sticky |
|
Datacenter |
High-speed, bulk operations | Data center IPs | Dedicated (same IP) |
We cover 195+ countries with residential proxies. For specific city or ASN-level targeting:
If you're switching from an affected provider, here's exactly what to do:
Before changing anything, capture your existing configuration:
Export these settings:
Document your usage patterns:
Consider what data passed through the compromised network:
|
Data Type |
Risk Level | Action |
|---|---|---|
|
Public web scraping (prices, listings) |
Low |
No immediate action needed |
|
Login credentials sent through proxy |
High |
Rotate credentials immediately |
|
API keys in requests |
High |
Regenerate API keys |
|
Session tokens |
Medium |
Clear sessions, re-authenticate |
|
Internal URLs exposed |
Medium |
Review access logs |
With Proxy-Seller:
Common configuration changes:
Most proxy formats are similar. Typical change:
Before (example 922proxy format):
proxy = "http://user:pass@922proxy.com:port"
After (Proxy-Seller format):
proxy = "http://user:pass@proxy-seller.com:port"
For popular tools:
|
Tool |
Config Location |
|---|---|
|
Scrapy |
settings.py → PROXY |
|
Puppeteer/Playwright |
Launch args --proxy-server |
|
Selenium |
proxy capability in options |
|
cURL |
-x flag or environment variable |
|
Octoparse/ParseHub |
Built-in proxy settings |
Run parallel tests for 24-48 hours:
Test checklist:
First week, track:
Use this checklist when evaluating any proxy provider. A legitimate provider should answer "yes" to most of these:
Different use cases have different risk exposures and migration priorities:
Your exposure: Low-medium. SERP data is public.
Migration priority: High (operational continuity)
What to verify with new provider:
Recommended product: ISP or Datacenter proxies for stability; Residential for heavily protected SERPs
Your exposure: Low-medium. Price data is public.
Migration priority: High (data freshness matters)
What to verify with new provider:
Recommended product: Residential proxies with sticky sessions
Your exposure: Medium. You may have accessed ad platforms with credentials.
Migration priority: High (verify no credential exposure)
Actions:
Recommended product: Mobile proxies (for mobile ad verification) or Residential
Your exposure: High if credentials passed through proxy.
Migration priority: Critical
Actions:
Recommended product: Mobile or ISP proxies (for account stability)
Your exposure: Depends on what you scraped.
Migration priority: Medium-high (operational continuity)
What to verify:
Recommended product: Match to your targets – Residential for protected sites, Datacenter for permissive targets
If you were affected by the IPIDEA shutdown:
Fill out the form and submit your migration request - we’ll follow up with next steps.
Questions? Contact us at enterprise@proxy-seller.com
Comments: 0