
 en
en  Español
Español  中國人
中國人  Tiếng Việt
Tiếng Việt  Deutsch
Deutsch  Українська
Українська  Português
Português  Français
Français  भारतीय
भारतीय  Türkçe
Türkçe  한국인
한국인  Italiano
Italiano  Gaeilge
Gaeilge  اردو
اردو  Indonesia
Indonesia  Polski
Polski There are numerous methods to conceal your IP address, each with its own advantages and suitability for different security needs. From VPNs and proxies to the more intricate TOR network, these techniques offer varying levels of protection and anonymity. This article will explore the most effective methods available in 2025 for hiding your IP address, ensuring you can avoid tracking and protect yourself from potential online threats.
An IP address is a unique string of numbers separated by periods (IPv4) or colons (IPv6) that identifies each computer, smartphone, tablet, or other device connected to the Internet or a local network. IPv4 addresses, like 192.168.1.1, and IPv6 addresses, like 2001:0db8:85a3:0000:0000:8a2e:0370:7334, are the two main types of IP addresses. These addresses are allocated to devices by internet service providers as they connect to the internet. Devices use their IP addresses to send and receive data, facilitating online activities such as loading web pages, sending emails, and streaming videos.
From an IP address like 123.45.67.89, you can derive several pieces of useful information using specialized tools and services:
A deeper analysis of an IP address, including examination of associated cookies, could reveal more detailed user data, such as social media profiles, hardware specifications like video card details, financial services used, and preferred online platforms.
This wealth of personal information accessible through an IP address is why many individuals seek to hide their IPs. They aim to enhance their online anonymity, reduce targeted tracking and profiling for advertising, secure their data against potential cyber threats, and access geo-restricted content.
Here are five common methods for hiding your IP address, each offering different advantages and levels of privacy:
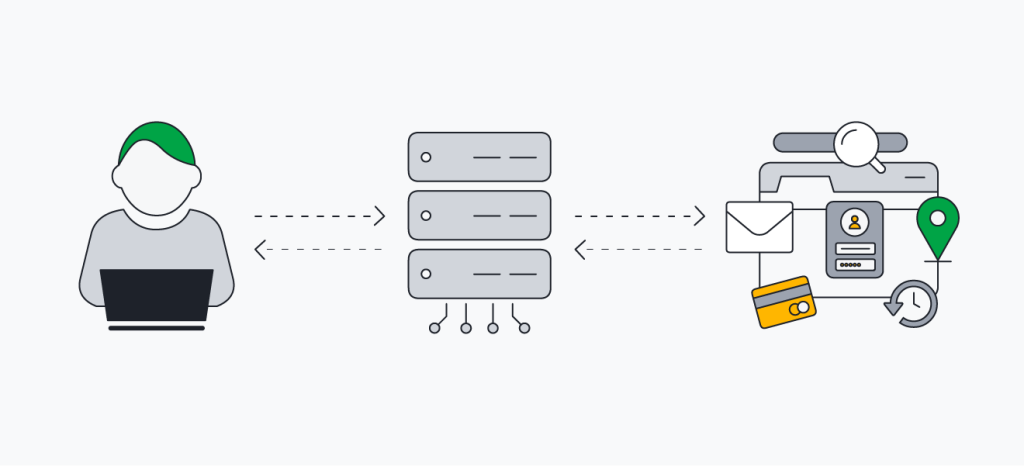
Using a proxy server involves routing your internet requests through an intermediary server, which then forwards these requests to their final destination. This means that the website or service you are accessing sees the IP address of the proxy server instead of your own. This method is particularly useful for maintaining anonymity online, bypassing geographic restrictions, or managing multiple accounts on platforms like Amazon, Instagram, YouTube, and more, where using multiple accounts from a single IP address might lead to account bans.
Proxies can also enhance browsing speed by caching data from frequently visited websites, thus reducing load times. They are also employed by organizations to monitor and restrict internet access, ensuring employees or network users can only access appropriate content.
For tasks that require advanced capabilities, such as web scraping, SEO monitoring, or software testing, using multiple or dynamic proxies is beneficial. Dynamic proxies, which regularly change IP addresses, are especially effective in evading detection from anti-fraud systems and solving captchas, thereby enhancing efficiency in handling extensive data tasks.
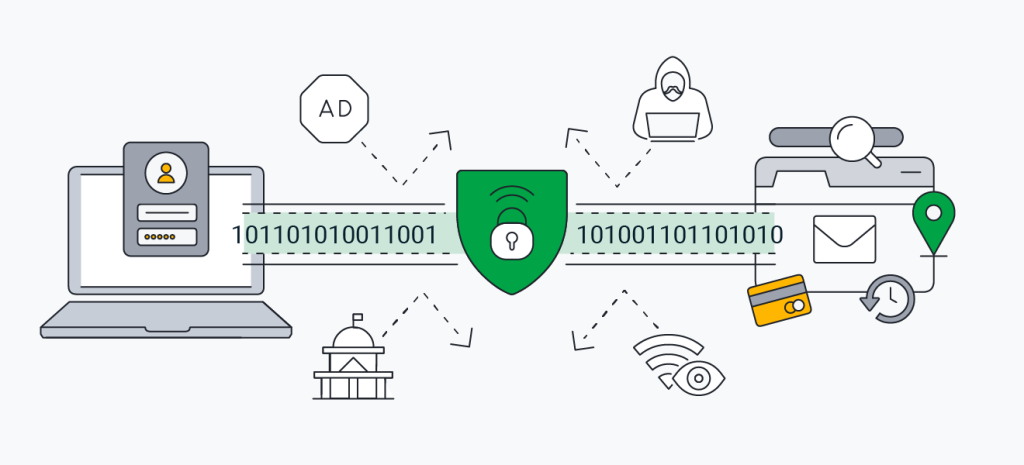
A VPN (Virtual Private Network) enhances your internet privacy and security by encrypting all your data transmissions, unlike proxies which simply reroute your internet traffic. Connecting to a VPN server assigns a new IP address, enhancing privacy by masking your actual IP address and location. This encryption makes your online activities incomprehensible to external parties, including your ISP and potential hackers.
While VPNs provide greater anonymity and security, they can reduce connection speeds and are generally more expensive than proxies. Additionally, VPNs lack the flexibility offered by proxies; they don't allow for specific routing controls where only certain applications or domains use an intermediary server, leaving other connections direct.
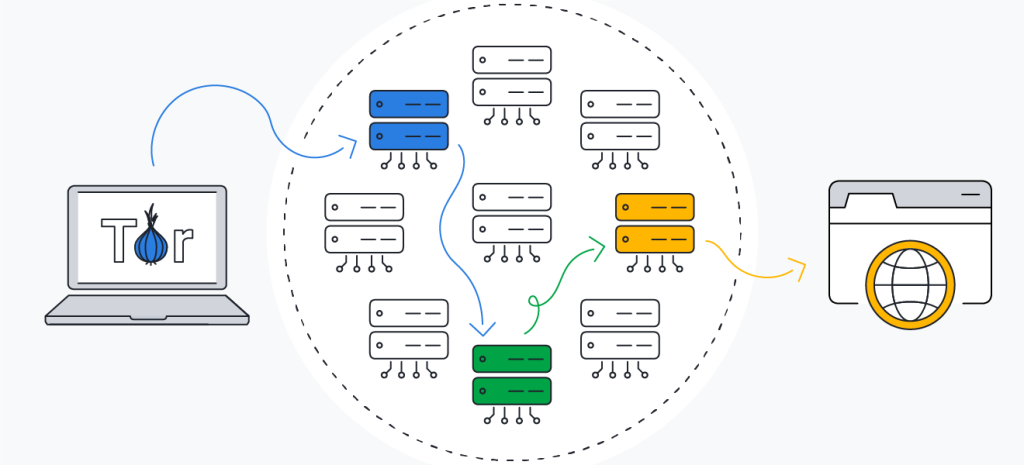
TOR, or The Onion Router, provides a high level of online anonymity through a complex network of relay nodes. This network encrypts user data multiple times and routes it through at least three nodes: the entry node, which knows the sender's address but not the destination; the intermediate nodes, which only know the addresses of the previous and next nodes; and the exit node, which knows the destination address but not the sender's identity. This structure ensures that no single node has enough information to trace the entire path of the data.
While TOR is excellent for privacy, its use significantly slows down internet speeds due to the elaborate routing and encryption process. Additionally, TOR's random assignment of exit nodes can make it inefficient for bypassing geographic restrictions, as it does not guarantee a connection from a specific region.
Setting up TOR is more complex compared to using simpler privacy tools like VPNs or proxies, requiring more technical knowledge and effort. This makes it less accessible for casual users who might prefer easier-to-use solutions for enhancing online privacy and security.
Using mobile networks is a quick way to change your IP address since each reconnection or movement across different cellular base stations assigns a new IP to your device. This inherent feature of mobile connectivity makes it a useful tool for enhancing anonymity online.
Mobile proxy servers expand these capabilities, allowing users to select IP addresses from various countries and mobile operators. This facilitates a higher degree of control over your online presence, offering benefits such as traffic filtering and enhanced privacy. Mobile proxies are highly regarded by various online platforms, which reduces the likelihood of encountering blocks or captchas, making them particularly useful for activities like managing social media accounts or SEO operations.
However, the main drawback of mobile networks is their relative lack of speed compared to wired connections. This can impact tasks requiring high bandwidth, such as video streaming or large file downloads, making mobile networks less suitable for such demanding uses.
Using free Wi-Fi in locations like restaurants, public transportation stops, train stations, or hospitals is another method to obscure your IP address. However, be wary of public Wi-Fi; these networks frequently lack security, leaving users exposed to hacking and data interception. Public Wi-Fi can temporarily change your private IP addresses to avoid tracking, but it’s advisable to steer clear of entering personal information or accessing online banking on these networks.
Hiding your IP address can help companies avoid access blocks to services, reduce the risk of DDoS attacks, and enhance infrastructure security. These issues are addressed using reverse proxy servers. Acting as intermediaries between clients and the company's website or application, reverse proxies protect against potential intruder attacks and distribute incoming traffic across multiple servers for load balancing. This distribution helps prevent server overloads and significantly boosts system performance.
For more detailed insights into how reverse proxy servers operate, their features, and their advantages, continue reading this article.
Hiding your IP address is legal, but it's crucial to be aware of potential limitations and consequences associated with various anonymity methods. Internet Service Providers (ISPs) may restrict VPN usage, and websites might reduce functionality for users connecting through public proxy servers. However, paid proxy servers typically do not face these restrictions.
Moreover, some countries have specific laws regarding VPN use. For instance, VPNs are entirely banned in North Korea, Oman, and Iraq. In China, VPN use is heavily regulated, with most foreign VPN services being blocked; only government-approved organizations can legally use VPNs.
To avoid legal issues and ensure safe internet usage, it’s important for users to thoroughly understand local laws and ISP policies before employing a VPN service or other methods to hide their IP address.
To effectively ensure that your IP address is hidden, you can use several methods:
If your IP address remains unchanged, this could mean the proxy server or VPN isn’t functioning correctly, or the connection hasn't been established. Check your connection settings and try again if necessary.
As of 2025, numerous methods exist for hiding your IP address, each providing varying degrees of anonymity. The choice of method should align with your privacy needs and objectives. Proxies are accessible and offer reasonable privacy for general use. VPNs enhance security with data encryption, though they may reduce connection speed. TOR provides the highest anonymity but significantly slows down the connection and isn't suitable for all uses. Mobile networks are limited by speed and may not be ideal for all tasks, while public Wi-Fi is fast but risky for sensitive activities.
Comments: 0