
 en
en  Español
Español  中國人
中國人  Tiếng Việt
Tiếng Việt  Deutsch
Deutsch  Українська
Українська  Português
Português  Français
Français  भारतीय
भारतीय  Türkçe
Türkçe  한국인
한국인  Italiano
Italiano  Indonesia
Indonesia  Polski
Polski As part of modern web development and systems administration, Nginx Proxy Manager setup is indispensable. It facilitates automated SSL certificate issuance and reverse intermediary server configuration via a user-friendly interface, thus easing the burden of complex configuration systems. This gives an edge to web developers of all degrees of seniority. Let us first focus on what NPM entails, how it differs from standard Nginx proxy, and what issues it solves.
To get the most out of this tool, it is important to first clarify the differences between the original Nginx, with which it is often confused, and the concept of a reverse proxy.
A cloud-based reverse proxy server facilitates a myriad of critical functions that include traffic filtering, load balancing, and concealing the actual workings of the internal servers from the client. This improves external security, internal reliability, and overall performance. So put simply, reverse proxies are server-side solutions as opposed to forward proxies which operate on the client-side.
It serves as software for a reverse and mail type intermediary server, a load balancer, and an HTTP cache. Nginx Proxy Manager is an application built off of the original Nginx’s source code. It acts as an additional management layer that administers the reverse functions.
This approach should not be confused with the direct proxies sold by us at Proxy Seller, which operate client-side and are used to route outbound traffic through a specific IP address. For example, ISP proxies provide stable static IPs and are typically chosen when predictable connectivity and long sessions matter. Residential proxies use IP addresses from real home networks and suit scenarios requiring a more natural traffic profile. These solutions are used for web access control, automation, data parsing, and managing outbound connections, not for handling inbound server traffic, as with Nginx Proxy Manager.
Along with the shared architecture and design principles, Proxy Manager differs from standard Nginx in several important ways. The differences are compiled in this comparison table summarized below.
| Feature | Proxy Manager | Nginx |
|---|---|---|
| Management Interface | Offers a visual GUI that simplifies intermediary server configuration | Managed via CLI using directives like proxy_pass, which require deeper technical skills |
| SSL Management | SSL certificate uploading and renewal is automated | Requires manual intervention from a system administrator |
| Configuration Access | Limited | Full access via terminal |
| Updates | Irregular | Regular updates and strong community support |
| Functionality | Some features only available in specific builds | Built-in tools suitable for complex and custom implementations |
| Scalability | Limited for large-scale, complex infrastructures | Better suited for scalable enterprise environments and high-load systems |
Before configuring proxying in this tool, it’s better to review its functional capabilities. Key features include:
Clearly, the tool not only aids in configuring the reverse proxy in Nginx, but also enables the administrator to restrict access to web assets securely.
The centralized management of various applications serves as one key functional example . This software solution offers a single control dashboard from which an administrator can manage:
As an example, a system administrator has the ability to add new sites, configure HTTPS, set redirects, and control access through a central management interface. Using a unified management interface decreases the chances of error and service disruption that manual configuration file edits introduce.
Moreover, Nginx Proxy Manager setup can enhance the security for cloud resources and servers by shielding them through some of its built-in capabilities like:
Consider a company with web apps (a WordPress site, REST API, control panel) hosted on a cloud VPS. To defend these apps from external threats and conceal the internal structure, a DevOps engineer configures the tool as described above.
Every operating system is compatible with this tool. In order to install and operate it, the following hardware configurations are recommended:
In addition, one will need Administrator credentials. If logged in as a guest, one will need to reboot with those elevated rights or obtain them from the PC owner.
sudo apt install docker.io -y
sudo apt install docker-compose -y
docker --version
docker-compose --version
mkdir ~/npm && cd ~/npm
nano docker-compose.yml
version: '3'
services:
app:
image: 'jc21/nginx-proxy-manager:latest'
restart: always
ports:
- '80:80'
- '81:81'
- '443:443'
volumes:
- ./data:/data
- ./letsencrypt:/etc/letsencrypt
docker-compose up -d
https://IP-address:port
Email: admin@example.com
Password: changeme
That’s it, the installation has been completed successfully.
The configuration involves major three steps:
Let us consider how this can be implemented step-by-step.
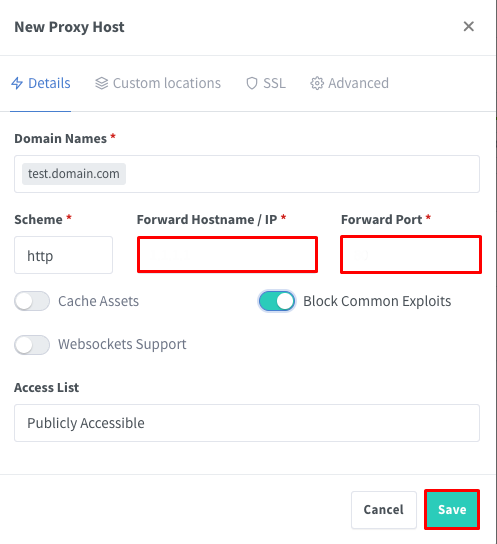
Navigate to the “Proxy Hosts” section, and from there select “Add Proxy Host”. A dialog with these entries will pop up:
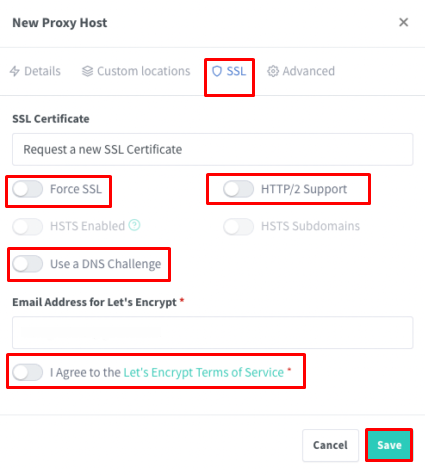
In the same window, navigate to the “SSL” section. Select “Request a new SSL Certificate” and enable the following options:
Click “Save”. The certificate will be automatically requested and installed.
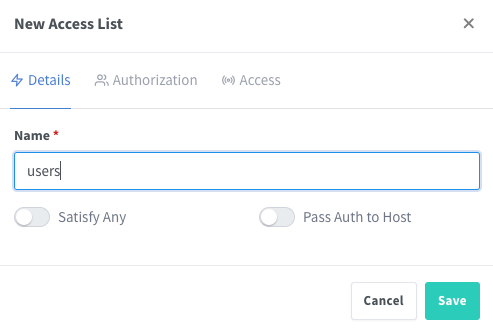
To create a new access list in Nginx Proxy Manager, go to the “Details” section. Assign a name like “users.” Note the “Satisfy Any” setting – if unchecked, users must fulfill all access conditions (authentication and IP match) which is more secure.
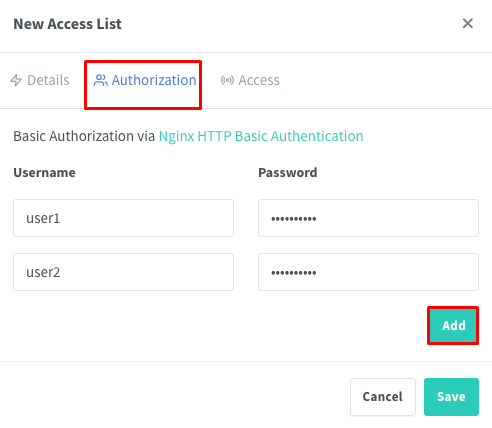
In the “Authorization” section, specify which users should have access and for each user set a username and password — this is basic HTTP authentication to access the site.
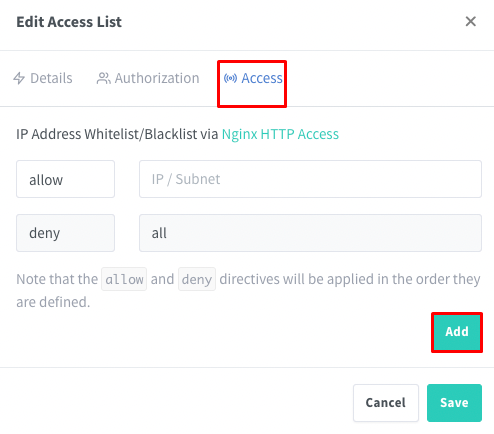
In the “Access” tab, enter IP addresses to be allowed or blocked access. This enforces access based on corporate network policies.
Once the access list has been created, navigate back to the settings for the target host and apply the newly created access list in the “Access List” field. From this point onward, user authentication will be required in relation to the site and access will only be granted if all conditions are fulfilled.
In reviewing this guide on Nginx Proxy Manager, it is evident that this is a multifunctional tool for setting up reverse proxies, managing SSL security, and controlling access to cloud resources. It is particularly useful for developers and systems administrators who require centralized and secure control of dozens of websites and services, as well as for personal use, like deploying a home server (NAS) or providing secure remote access to a local area network.
The core advantages of this manager include its broad compatibility with all operating systems, streamlined management that does not require command line interaction, and rapid configuration of proxies and SSL, which are some of its primary advantages.
Comments: 0