
 en
en  Español
Español  中國人
中國人  Tiếng Việt
Tiếng Việt  Deutsch
Deutsch  Українська
Українська  Português
Português  Français
Français  भारतीय
भारतीय  Türkçe
Türkçe  한국인
한국인  Italiano
Italiano  Indonesia
Indonesia  Polski
Polski Nowadays, people and businesses are increasingly using intermediary servers for privacy reasons, circumventing region-based restrictions, and automated data retrieval tasks. Unfortunately, not all websites welcome such connections. In an effort to protect their servers from DDoS attacks, bots, content scraping, and other malicious activities, many websites monitor and restrict traffic routed through proxies. This often leads to the following warning: “anonymous proxy detected.” This indicates that the security system of the website has detected an intermediary server and therefore blocked access.
Let’s analyze what an anonymous proxy is, the reasons behind this error, and methods to bypass it while retaining essential access.
Intermediary servers can be classified into three categories based on the level of anonymity: transparent, anonymous, and elite. A server is considered anonymous based on the level of identification it reveals to the target website, as well as if it identifies itself as a middleman.
An “anonymous proxy detected” meaning error occurs when a site’s security system evaluates the HTTP headers, traffic patterns, address reputation, and other intricate details, and considers the use of a node as sufficiently dangerous. Websites often combine their own behavioral detection algorithms with reputation-based blacklisting external databases of known malicious IPs.
Such servers become increasingly more common in today’s browsing environment, understanding their limitations becomes equally as important. This warning arises from them being used, but the servers themselves do not trigger this warning. It is remotely possible for them to trigger warning signs as a result of their detectable traits.
To safeguard information and circumvent geo-restrictions, some users resort to intermediaries that conceal their addresses. However, if such proxies are not configured properly, they may trigger a website’s security systems. In addition to improper configuration, several other reasons can lead to this error. Here are the main ones:
The warning “Anonymous Proxy Detected” can arise due to both the use of publicly available IPs and improperly configured parameters. To optimize the chances of avoiding this issue, it is best to follow the instructions stated below.
There are a number of ways on how to fix anonymous proxy detected errors. A specific approach will be effective depending on whether the user has access to a paid or free intermediary server, the environment where the error occurs, and the user’s technical expertise. Let us explore several solutions, beginning with the simplest and progressing to the more complex, including the utilizing of Python scripts.
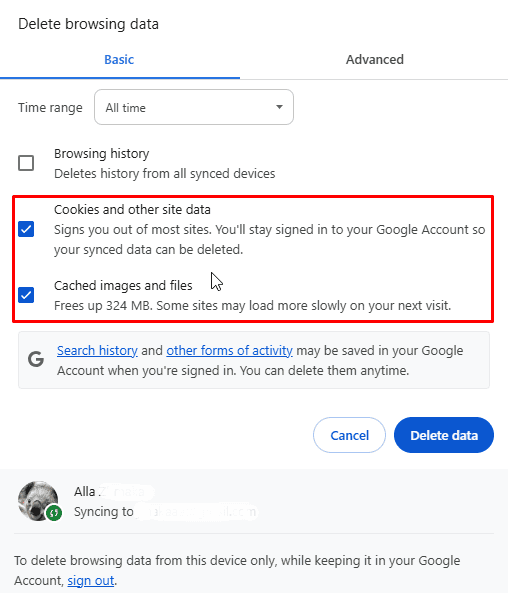
Cookies and cache files allow websites to recognize users and track repeat visits. Therefore, even with the use of an intermediary, the data stored on your browser may reveal your true identity and result in the triggering of the error.
Clearing cache and cookies is uniform across different browsers. Go to the browser’s Settings, navigate to Privacy and Security, and select Clear Browsing Data. You may also search through the settings for quicker navigation.
WebRTC has the capability to expose your genuine IP address even if you are connected to a proxy or a VPN. This is because of its peer-to-peer connection model that sends IP and other connection information in a raw form.
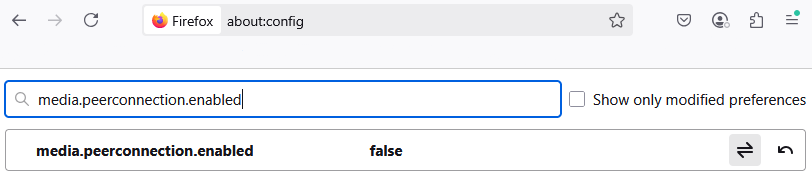
To turn off this feature, you need to set the value to 'Disabled' on your browser. Access methods differ based on the browser in use.
Visit the Chrome Web Store and look for the extension named “WebRTC Control.” Following installation, the plugin should be showing a blue icon which indicates that the WebRTC blocking feature is on.
Enter about:flags in the URL field. Search for WebRTC. Find the “Hide my local IP address when using WebRTC” option and check it on.
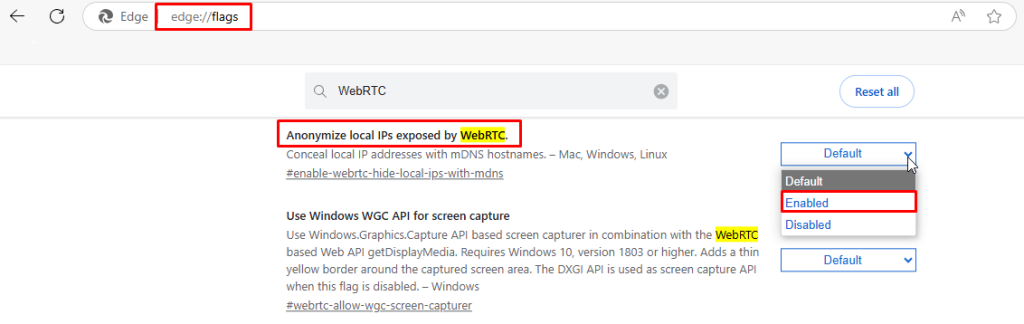
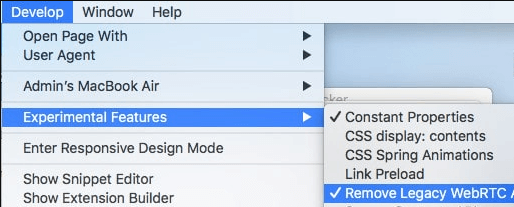
Note: This workaround is only applicable for macOS versions earlier than 10.14.4. For anonymous proxy detected iPhone fix with iOS 12 and later, there is no way to block WebRTC – this option is unavailable due to Apple restrictions.
To mitigate the chances of being blocked, as well as to provide uninterrupted access to target resources, such types provide the best solution. These servers use addresses assigned through internet service providers to real people, so their traffic is perceived by websites as normal user traffic.
A large number of requests from a single address increases the chance that the interaction will be construed as suspicious. As a result, the connection may be terminated by the system’s security mechanisms, especially if the data seems to come from automated sources.
In the case of automated activity, a straightforward solution to the “Anonymous Proxy Detected” problem is rotation. It is vital to differentiate type of such nodes:
Below is an example of a Python script that utilizes rotating proxies:
import requests
import itertools
import time
# List in the format "http://username:password@ip:port"
proxies_list = [
"http://user1:pass1@192.168.1.101:8080",
"http://user2:pass2@192.168.1.102:8080",
"http://user3:pass3@192.168.1.103:8080",
]
# Create a cyclic iterator
proxy_pool = itertools.cycle(proxies_list)
# Headers to simulate a real browser
headers = {
'User-Agent': 'Mozilla/5.0 (Windows NT 10.0; Win64; x64)'
}
# Target URL
target_url = "https://httpbin.org/ip"
for i in range(10): # Example: 10 requests
proxy = next(proxy_pool)
proxies = {
"http": proxy,
"https": proxy,
}
try:
response = requests.get(target_url, proxies=proxies, headers=headers, timeout=10)
print(f"[{i+1}] IP via proxy: {response.json()['origin']}")
except requests.exceptions.RequestException as e:
print(f"[{i+1}] Error using intermediary server {proxy}: {e}")
time.sleep(2) # Delay between requests (can be adjusted)
This script iterates over a list of intermediaries and uses the addresses provided in the list to send requests to https://httpbin.org/ip, which exposes the external IP address in use. It also introduces delays between the switches to minimize the risk of detection as suspicious.
Chaining them is a method to enhance anonymity by increasing the number of sequential intermediate servers utilized on a connection.
Under normal circumstances, your device connects to a basic one node which connects to the target website. In this case, however, the connection will be through a chain of them. The flow of traffic for this scenario is as follows: Client → Proxy 1 → 2 → 3 → Website.
Because each intermediary conceals the information of the one before it, anonymity and resistance to surveillance are significantly improved.
The simplest way to configure such a chain is through Proxifier. In the application, you can add a list of addresses and specify the order of how the traffic should flow.
Previously, we discussed the reasons behind the “Anonymous Proxy Detected” error and its implications. The main cause of this error is the use of anonymizers, especially free ones that are exploited and abused which in turn get blacklisted. To avoid this problem, a proper solution needs to be sought after. The following lists important tips that one should consider how to choose a proxy effectively:
The error “Anonymous Proxy Detected” is mostly triggered when a user employs an IP address with a bad reputation, commonly found to be public, previously blocked, or misconfigured. It shows that the site is aware of the usage of an intermediary and has blocked access for security purposes.
While some technical changes may help, such as header modifications, DNS/WebRTC leak repairs, or rotation implementation, the best approach is still the use of verified private proxy infrastructure. These solutions mask and anonymize the location while also protecting against detection and access restrictions, ensuring consistent operation and fortifying proxies for cybersecurity applications.
Comments: 0